Intune - Using Access Packages to Enable User Device Enrollment

Many organizations use device compliance with Conditional Access to provide protection against MFA capable phishing attacks such as Modlishka, evilginx2, or @mrd0x's browser in the browser attack. This protection works well because Conditional Access uses certificate based authentication with the device and pulls compliance data from Intune, and the attacker doesn't have those... until they do :(
Unfortunately, we don't currently have a way in Conditional Access to use Block with User actions, but at least we can enforce MFA, including using the new Authentication strengths. Even when we enforce MFA for enrollment, an attacker equipped with an MFA'd token can register their own device and gain access. While it's true this creates a lot of noise for detection, unless Identity Protection detects this, it's unlikely many are effectively paying attention to this...
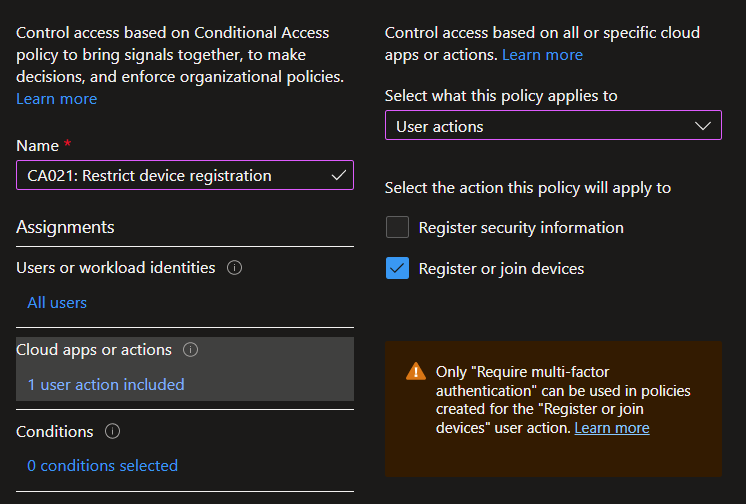
So what else can we do? Well, Intune has a feature called Enrollment device platform restrictions where we can prevent users from enrolling devices unless they are a member of a group, and we can define criteria for what they can enroll. When combined with another feature called Enrollment device limit restrictions, we can define policies such as limiting each user to one mobile device.

I realize this likely won't be a viable option for many organizations who encourage or rely on BYOD, and this article is really aimed at those who either need to lock down their environment a little more or are looking for ways to open up their environment a little more but still have some checks and balances.
For some awesome conversations and insights on this type of topic, check out the Twitter thread below.
Do you allow users outside of IT to join devices to Azure AD?
— 🔜 Jason? (@el_jasoon) November 10, 2022
OK, but I really don't want to micromanage tickets to put users in groups so they can enroll devices... Wouldn't it be great if we could automate it, maybe have an approval process? Welcome to Access Packages! :)
Access Packages in Identity Governance
Access Packages allow us to group access to things like Groups, Teams, Enterprise Applications, and SharePoint sites into an entitlement, and it just so happens that Intune restrictions are based on user groups. Our general process here will be to create a group, create an Access Package for membership in the group, and use the group for device enrollment restrictions (or device limit restrictions or both).
Create the group
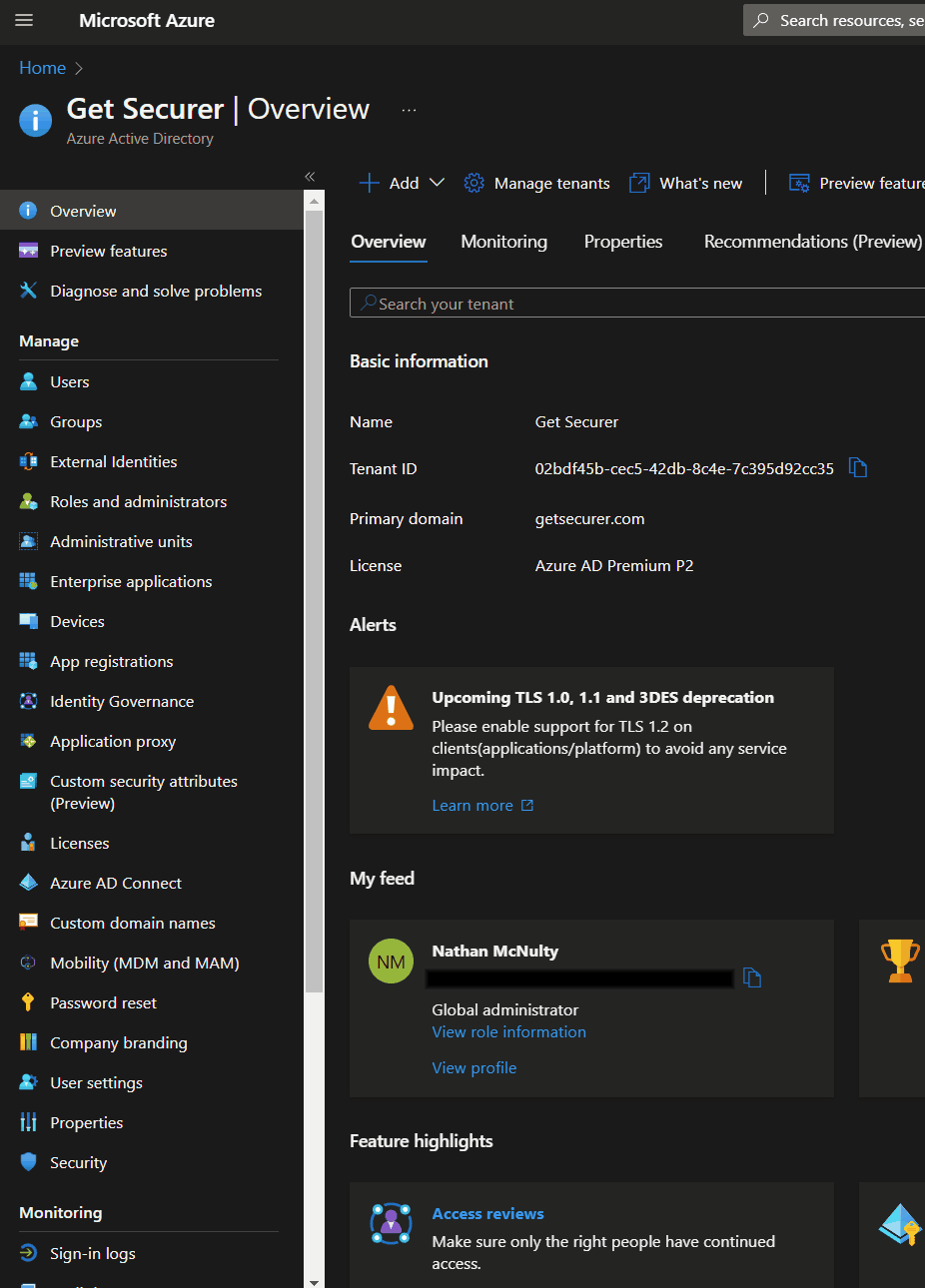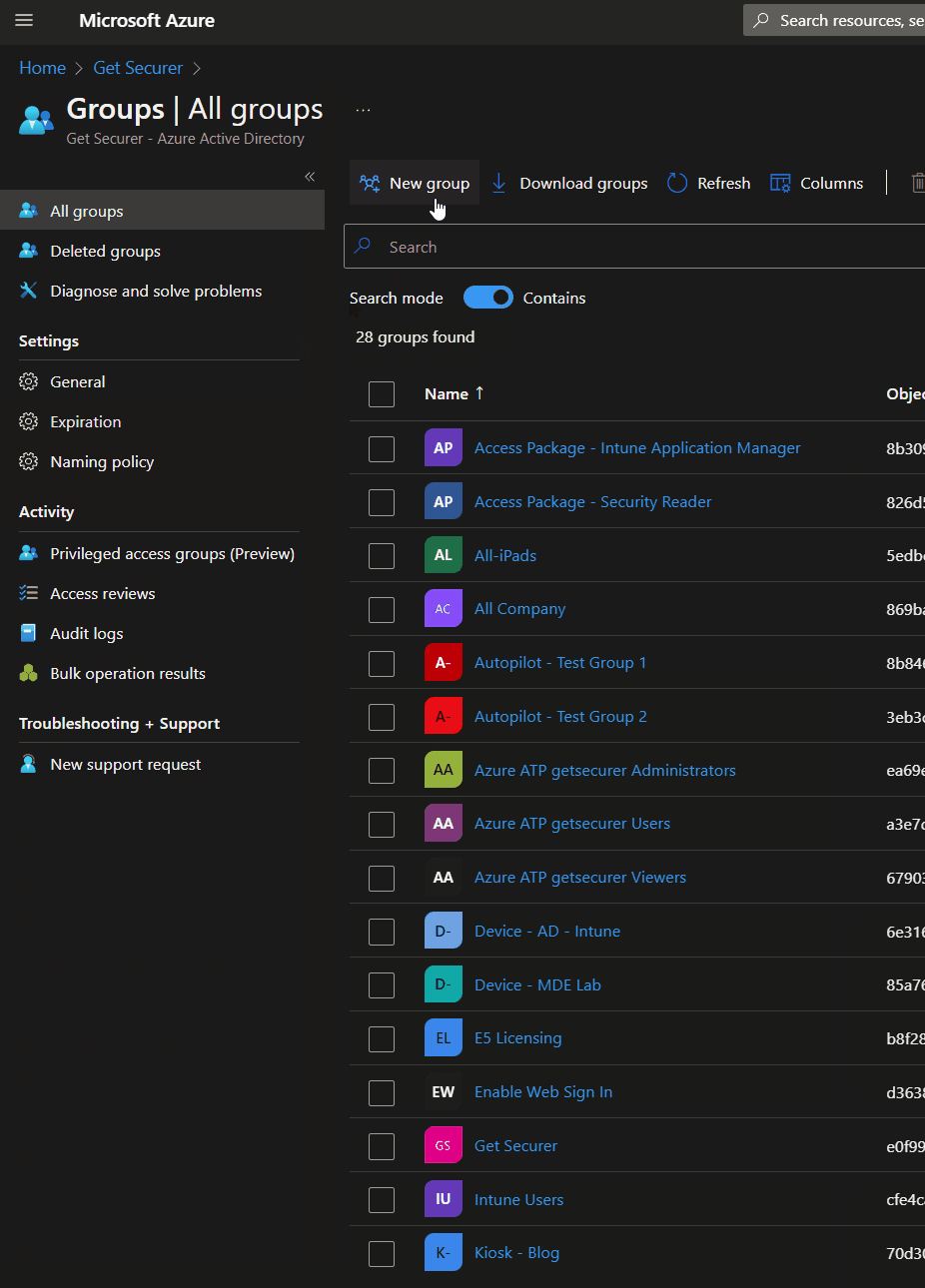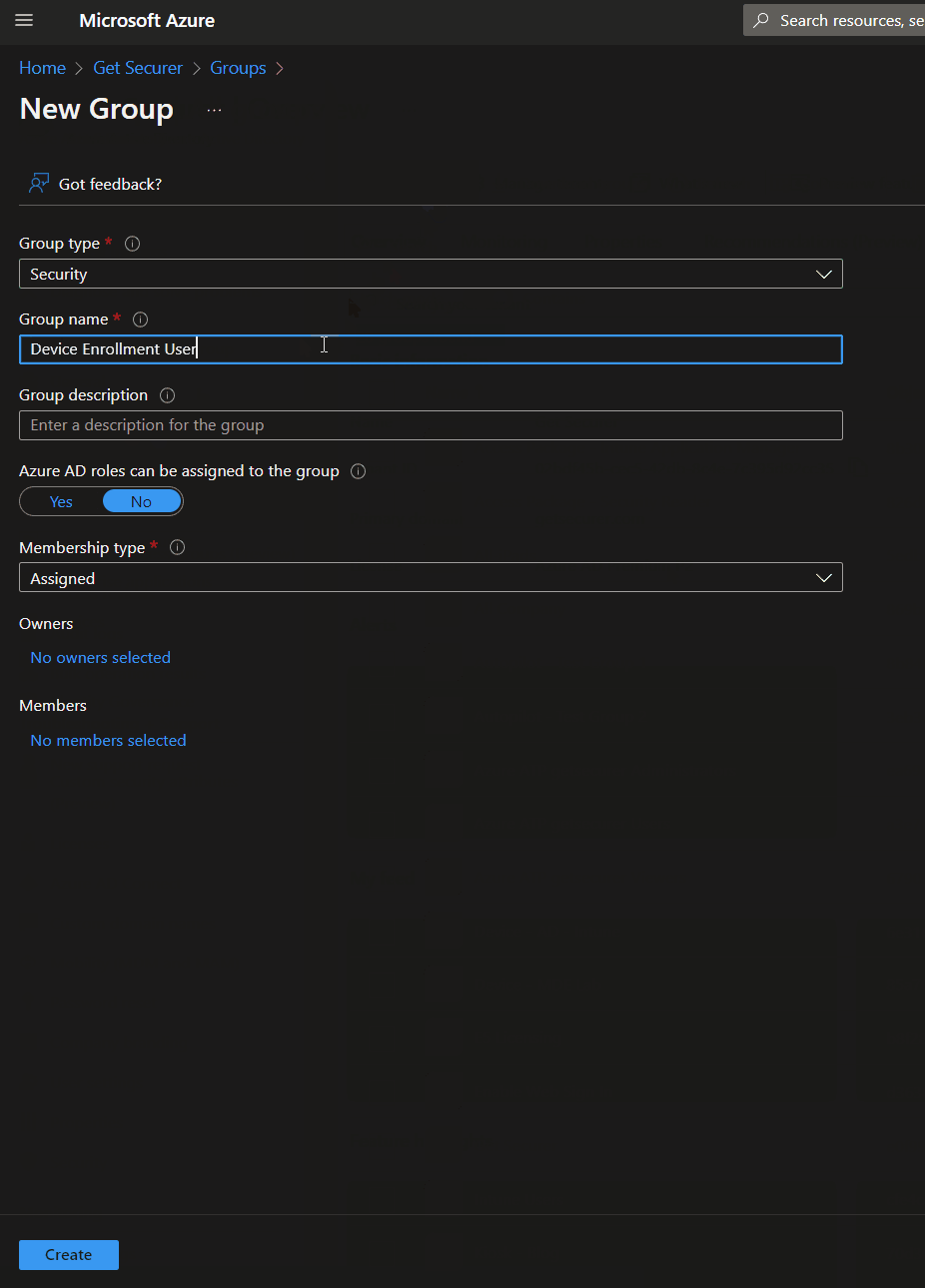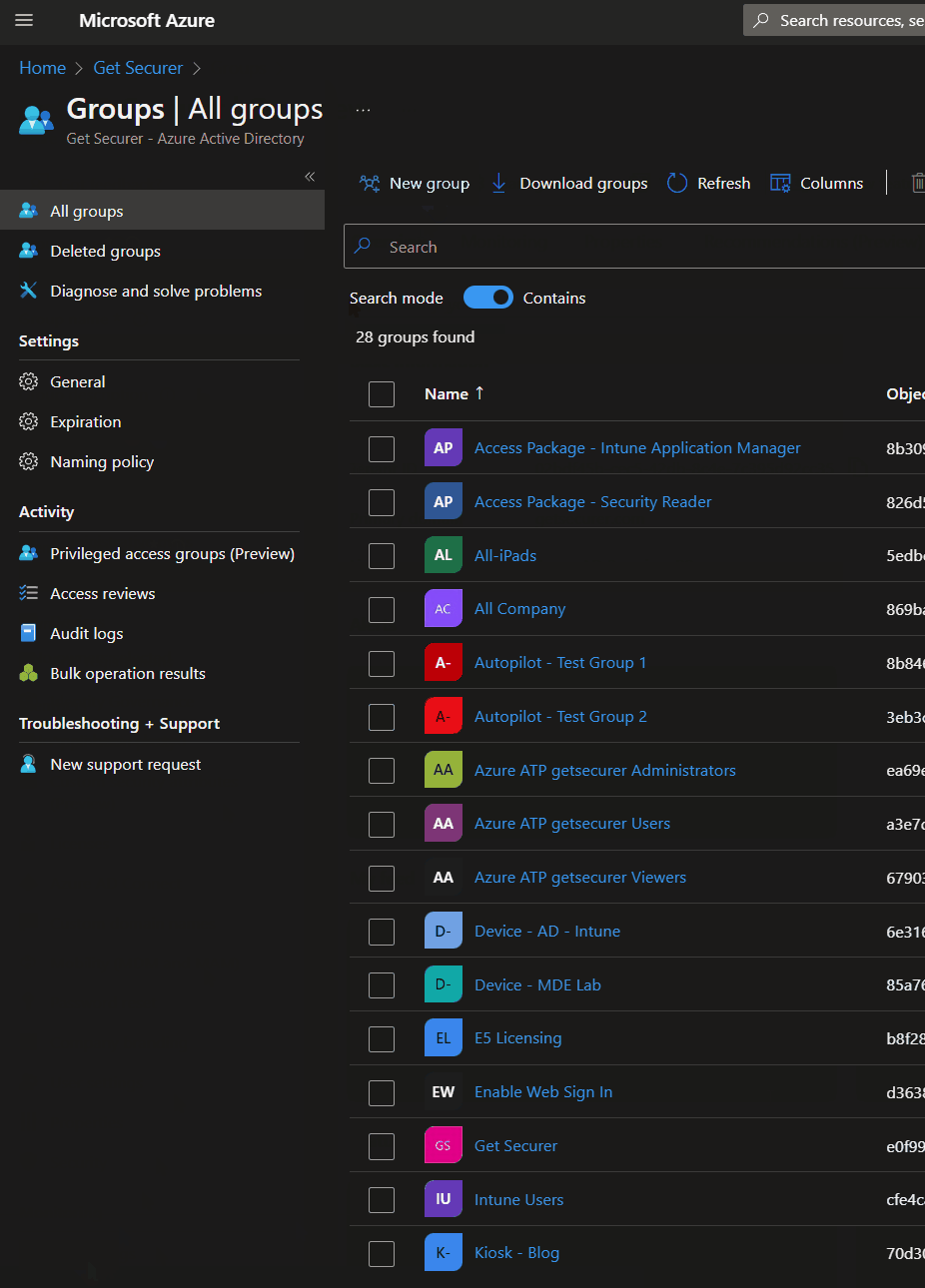
First, let's create a security group called Device Enrollment Users in Azure AD
Create the Access Package
Now, let's create an Access Package. Go under Azure AD, Identity Governance, Access Packages and click New access package. Provide a name and description (both are required), then click Next: Resource roles. Now click Groups and Teams, search for the security group we created, add it, and set Role as Member (if you miss this like I always do, creating the package will fail and send you back here to fix it). Click Next: Requests and review the options.
It's likely most orgs will want to make this entitlement available to all members in the directory, but you can limit scope to a security group if you want. You can decide if users can self-service or if you want an approval workflow, and it can even go up to 3 approvers. Note that admins can always manually assign users to this access package ;)
When done, click Next: Requestor information and decide if you want to ask the user any questions to help with the approval process (or leave it blank). Now click Next: Lifecycle, and decide if you want to require renewal and what that might look like. Here we can also add Access Reviews if you really wanted to clean up inactive users from the group. Click Next, Next, Create when finished.
Now, a quick but important note is that we could automate the removal of the user from the group after a certain number of days. For a simple example, it might be worth considering allowing users request without approvers and then remove them from the group after 7 days. Your users receive notifications, so malicious requests would be seen, and the audit logs also provide us with actionable data.
Configure Enrollment device platform restrictions
The final step is to go to Intune and set up Device enrollment restrictions. Head over to intune.microsoft.com and go under Devices - Enrollment device platform restrictions, then click Create restriction under Android restrictions. You will need to repeat the following process for each platform.
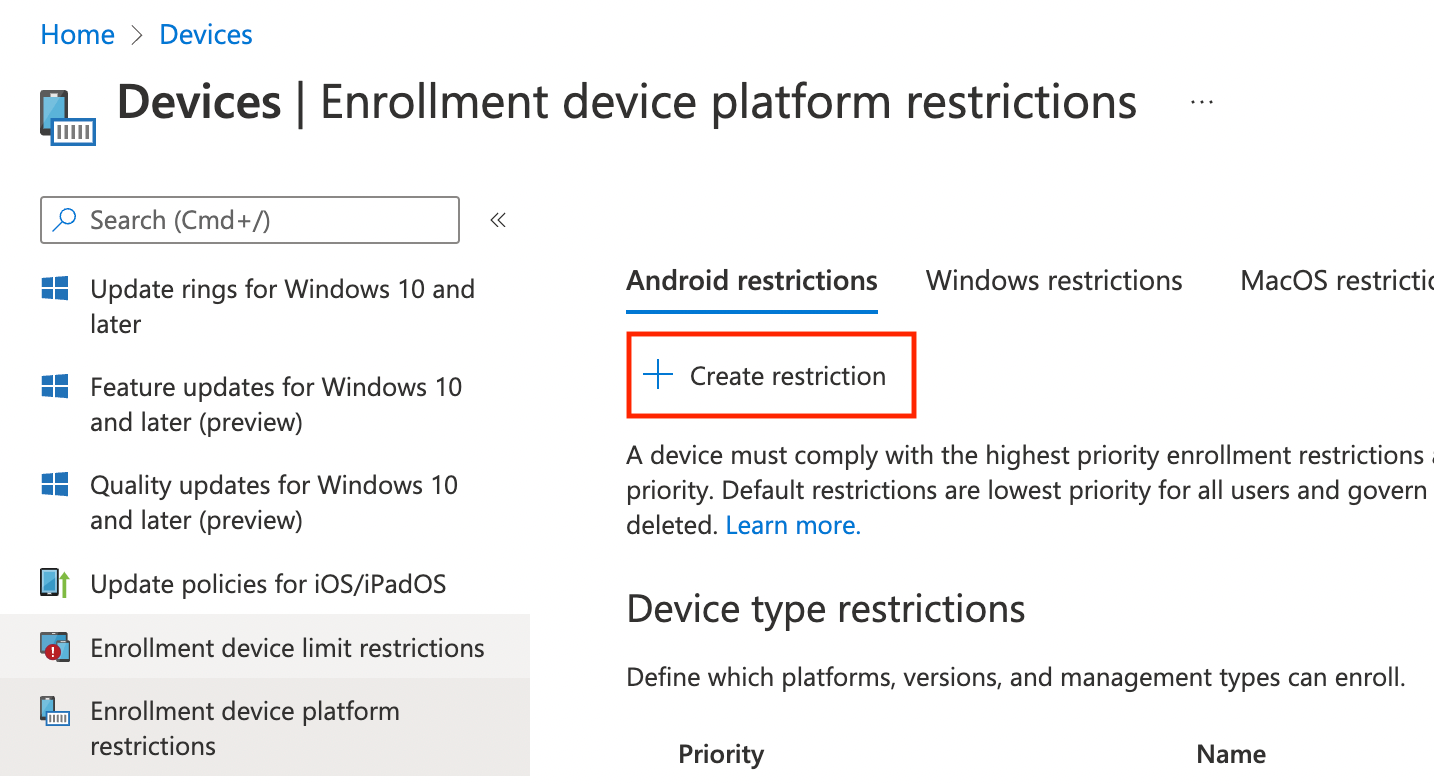
Provide a name for the policy, such as Device Enrollment Users, then click Next. I recommend blocking Android device administrator as it's a poor experience and will likely lose support. Apply any other restrictions you want, such as minimum OS version, then click Next. Apply scope tags if you use them, then click Next.
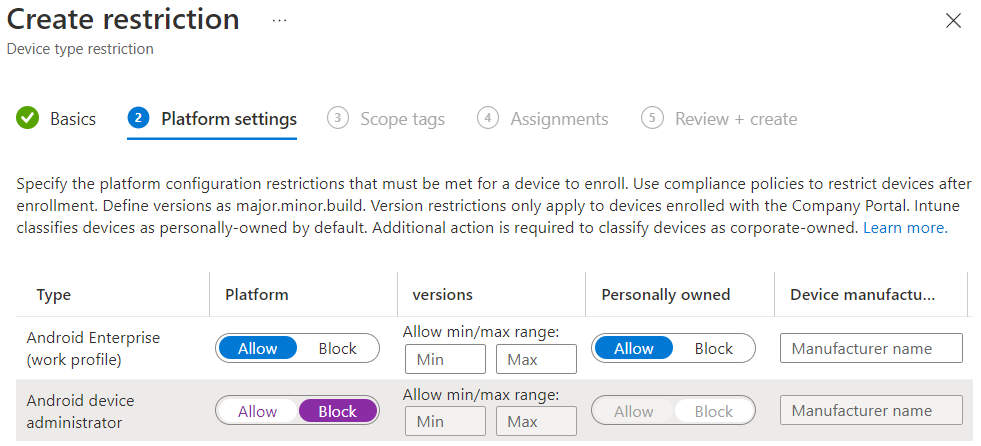
For Assignments, click Add groups, search for your group, click on it to select it, then click Select. When finished, click Next, then review the settings and click Create on the Review + create screen.
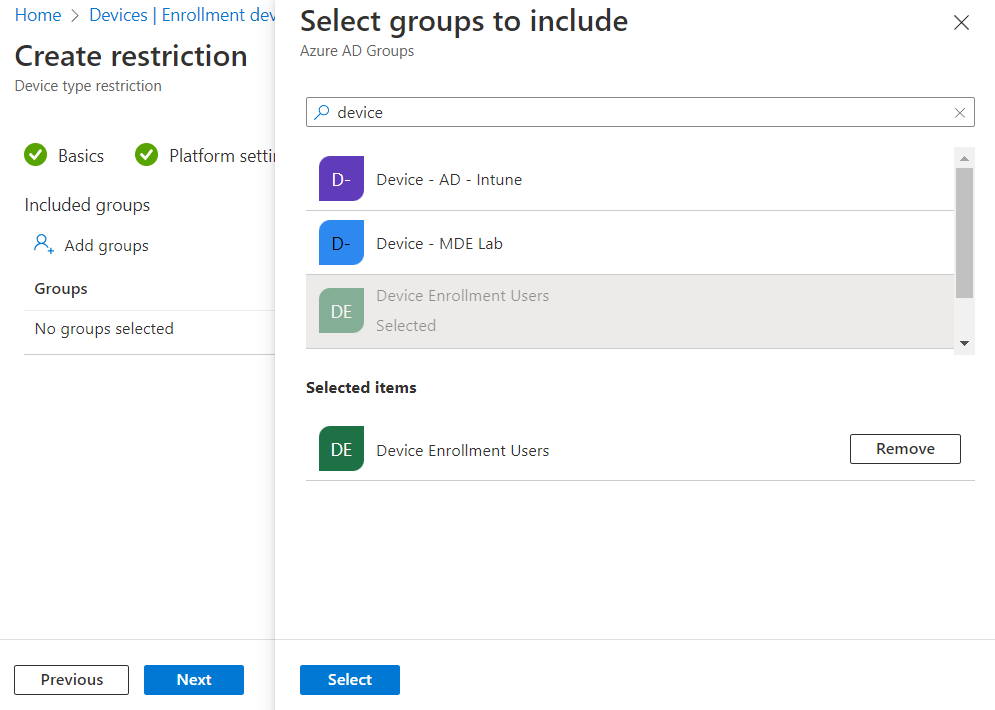
Once you have done this for all platforms, we need to edit the Default policy. To do this, click All users on any of the restrictions tabs.
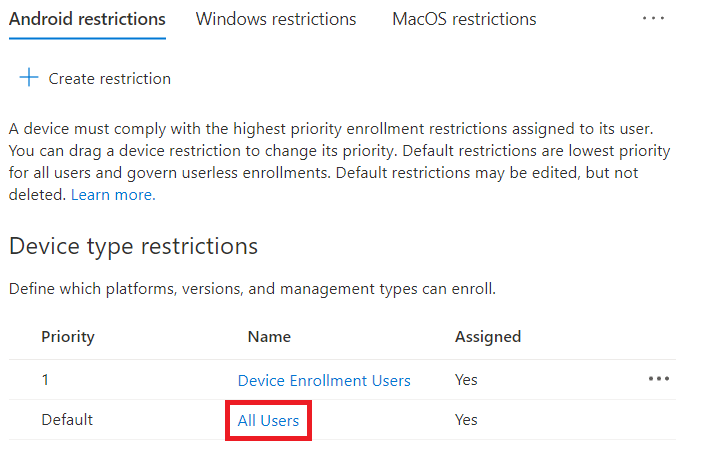
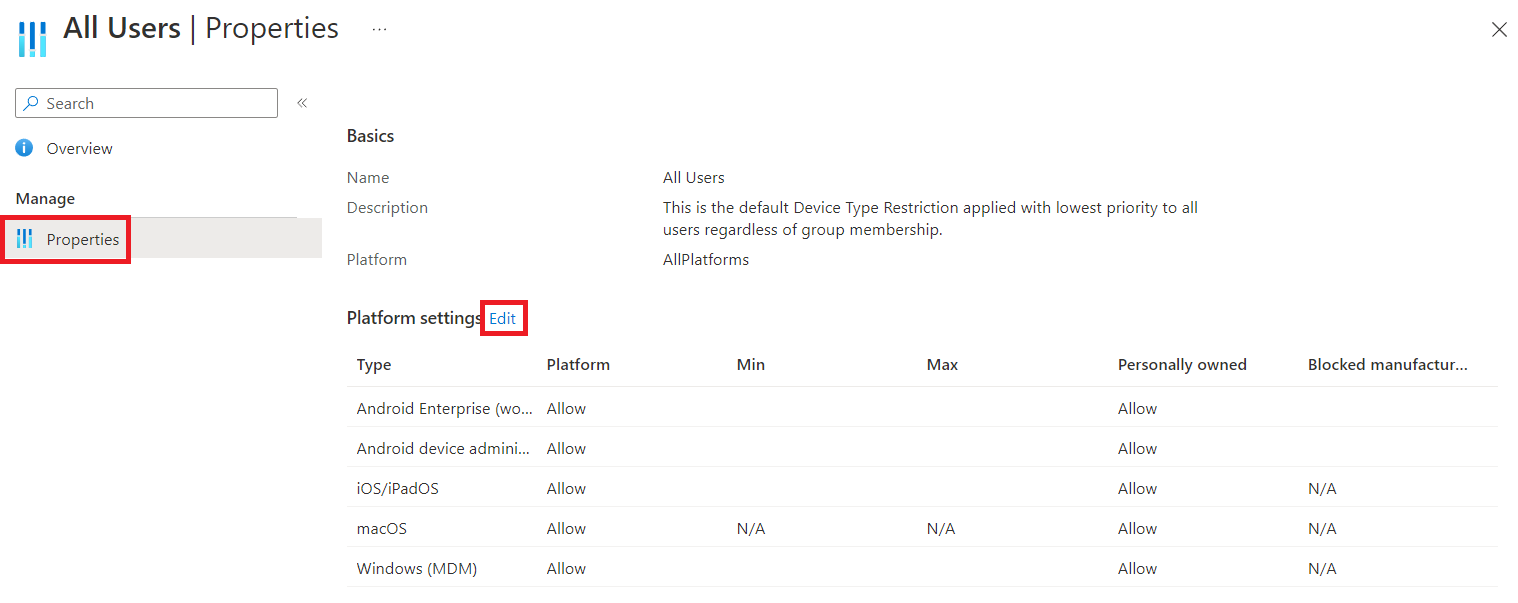
Next, click Properties, then click Edit next to Platform settings
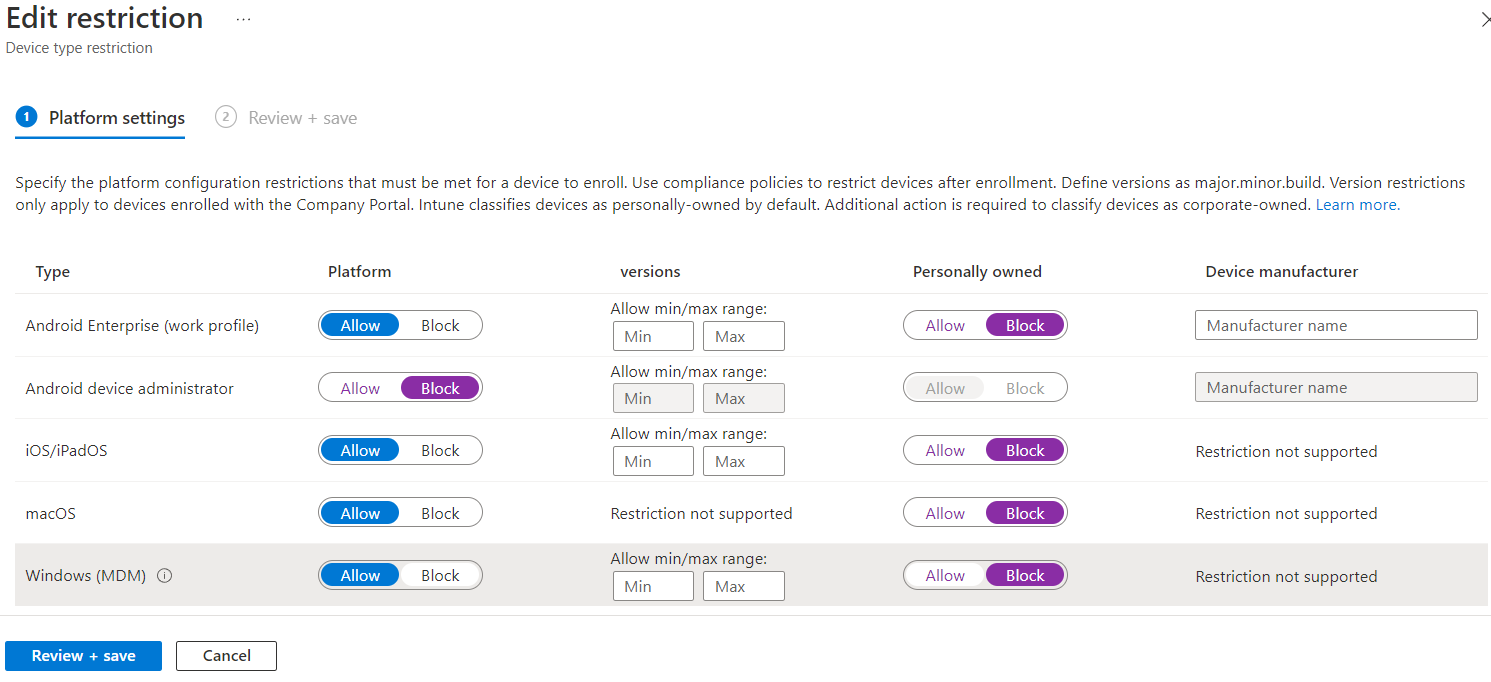
Finally, we can change all Personally owned to Block, and while we're here, I would recommend blocking Android device administrator as well. If you have any OS version or manufacturer restrictions you'd like to apply to Company owned devices, make those changes as well. Click Review + save, then click Save.
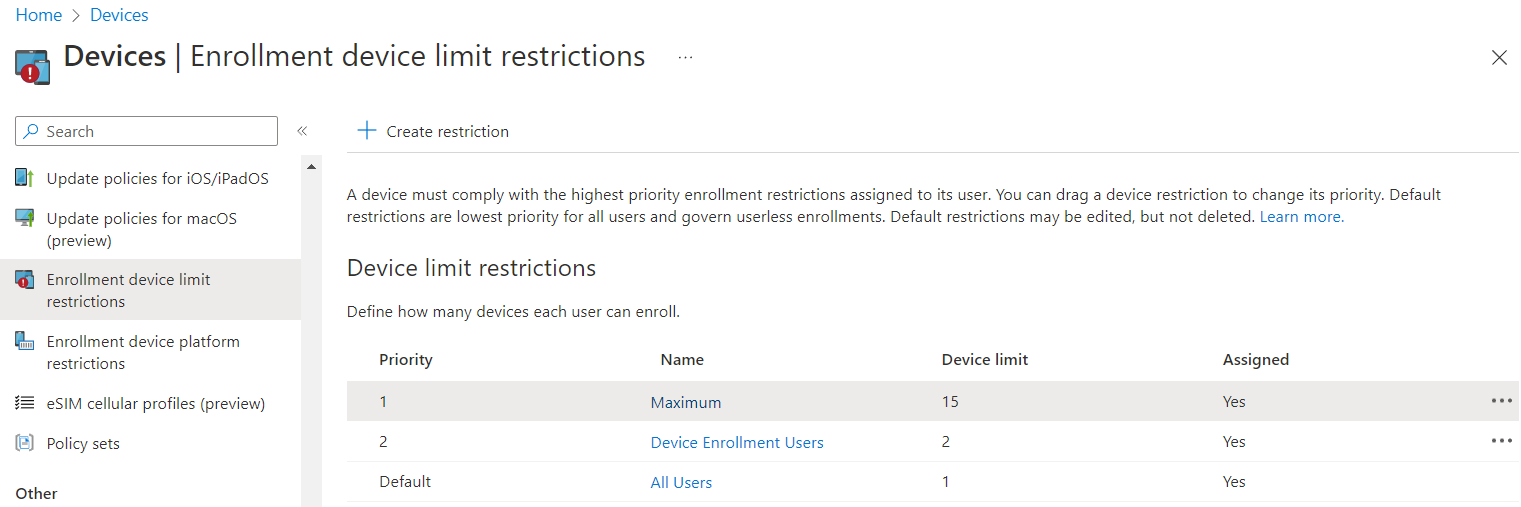
We can optionally adjust the number of devices users are allowed to enroll under Enrollment device limit restrictions. This restriction only applies at the time a device is enrolled, so we can limit users to 1 device by default, then allow more by putting them in a group with a higher priority restriction.
Under Devices - Enrollment device limit restrictions, click Create restriction.
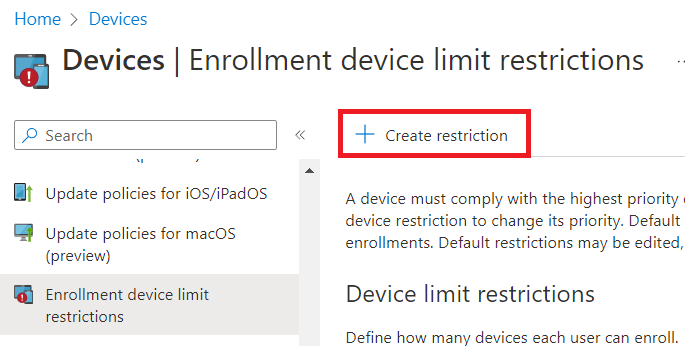
Provide a Name for the restriction, then click Next. From the Device limit dropdown, select the number of devices you would like to limit users to using this method (can use another restriction with a different group for even higher numbers if desired), then click Next. Add scope tags, then click Next.
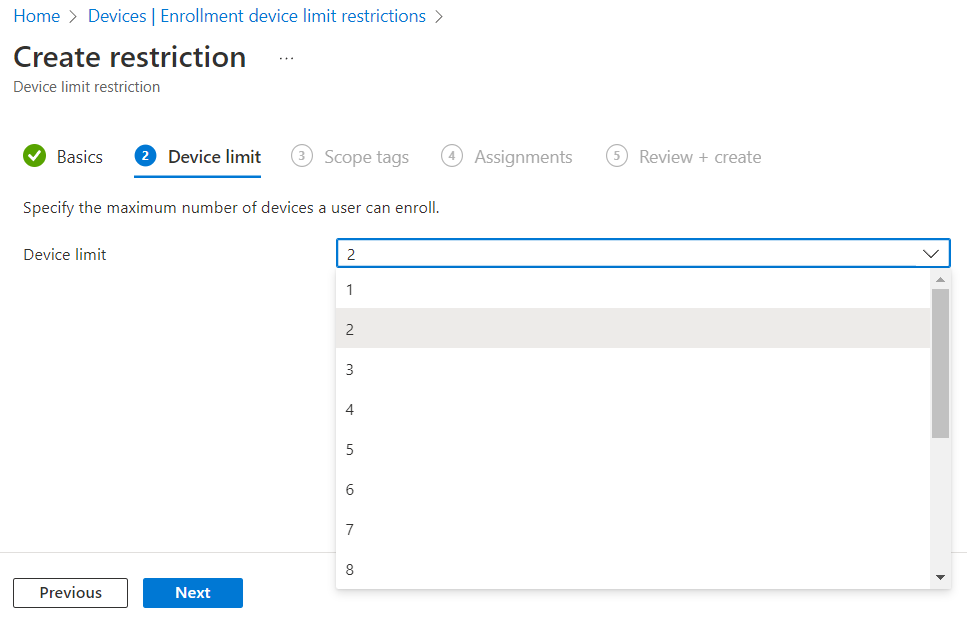
For Assignments, click Add groups, search for your group, click on it to select it, then click Select. When finished, click Next, then review the settings and click Create on the Review + create screen. You should now see your restriction with a priority number, and the lowest number applicable to a user wins.
End User Experience
With the processes built, it's a good idea to test and make sure everything works as expected. This also gives us an idea of what the end user can expect so we can create documentation and communicate clearly.
Head over to MyAccess (myaccess.microsoft.com or aka.ms/my-access), and you should now see the access package listed. Selecting the Access Package should bring out the dialog on the side where we can click Request access.
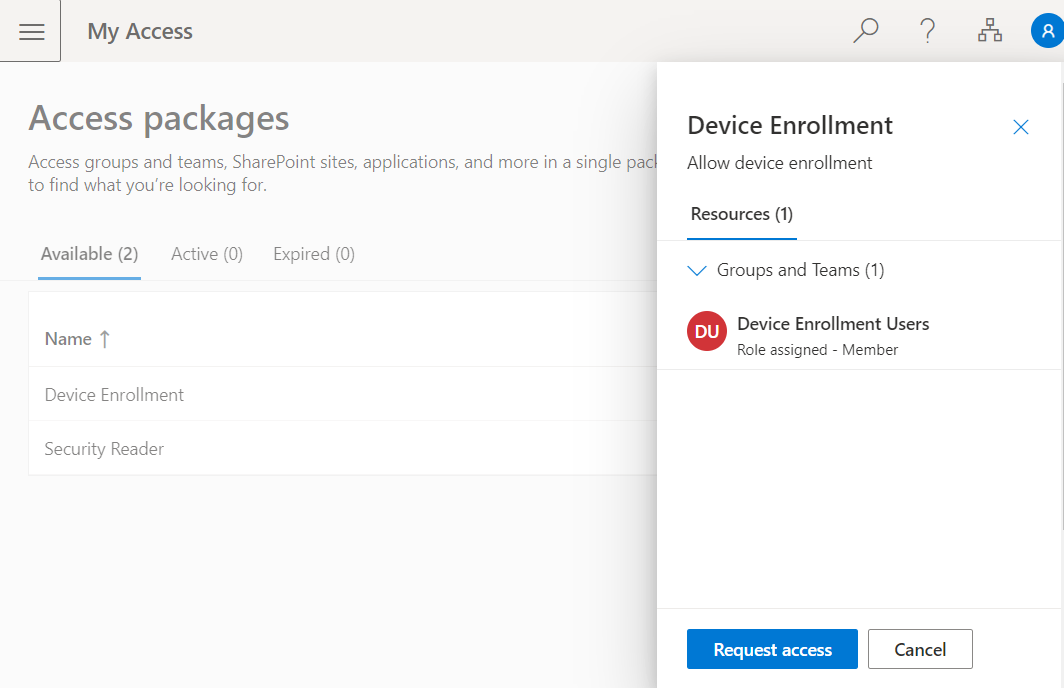
Depending on the settings you configured for the access package, the user experience may look a little different. As you can see here, I put in a business justification for the request which then either grants access to the group or kicks off the approval workflow as configured.
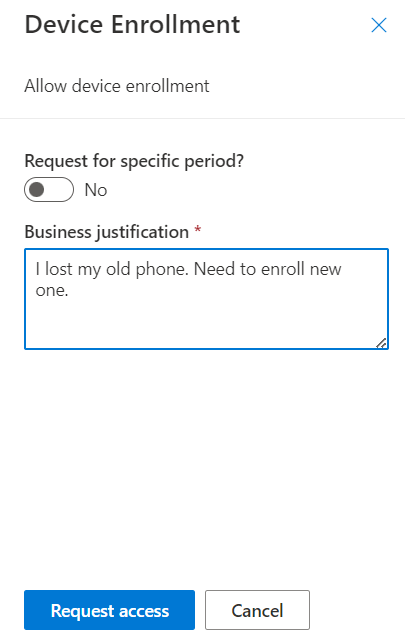
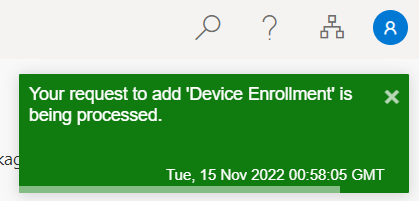
Once the user clicks Request, they should see a confirmation, and we should see it in Azure AD :)
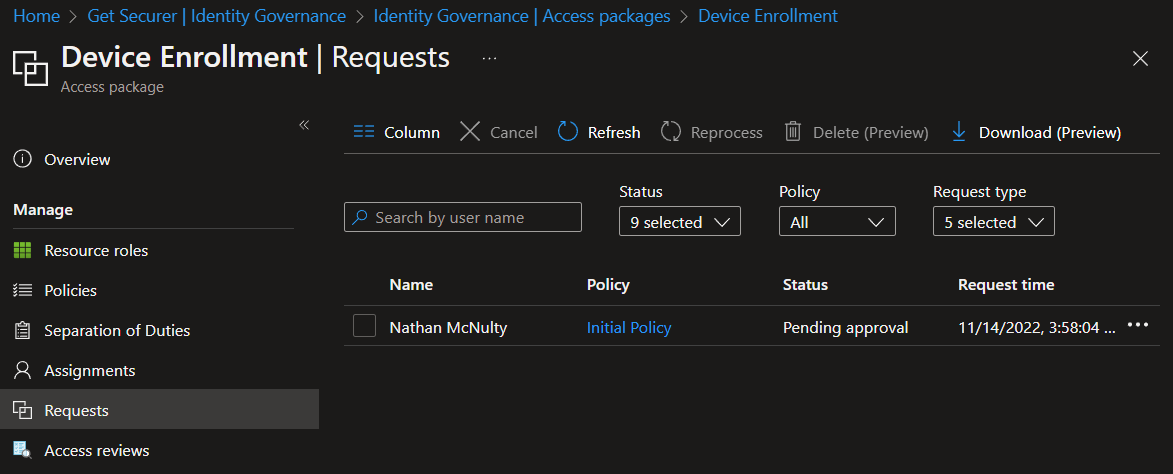
Admins are not able to approve their own requests, but they can explicitly assign themselves to Access Packages if needed.
Hopefully this gives you an idea of how Access Packages can be used, specifically with Intune but also more globally. Consider that we could use this group for assigning licensed applications, for exclusions from Conditional Access policies, or even access to on-prem applications exposed through Azure App Proxy.
