Intune - Edge in iOS Kiosk Mode

Getting a web app to run in Edge in Kiosk mode on iOS has been a journey, so here's a guide on how I did it :)
— Nathan McNulty (@NathanMcNulty) May 24, 2022
Every example I found online used either a 3rd party app or Safari with a Web Content Filtering policy, but Edge was needed for a specific authentication requirement
I recently had a request to lock iPads in Kiosk mode for use with a web app, but we needed to use Edge for specific authentication requirements. Every example I could find used either a 3rd party app or Safari with a Web Content Filtering policy, so it was time to see if I could figure out how to do it with Edge :)
During my research, I found this Microsoft Doc on Manage Edge for iOS and Android with Intune, but it was not clear to me on how I could achieve what I wanted. Initially I saw Kiosk Mode was only available for Android, but I decided to try it anyway to see if the Docs just hadn't been updated. While it didn't work, the process did give me other ideas to play with resulting in the following solution:
We will need a kiosk user assigned to a device because we need an App configuration policy for managed devices and another App configuration policy for managed apps, and of course we'll need Edge deployed as well. Once all of that is set, we push a Configuration profile to enable Kiosk Mode specifying Edge as the Managed App, and we should see Edge launch, log in as our Kiosk user, and have the web app load :)
Create a Kiosk User
First, let's create a kiosk user that will be used to sign into the iPad. We need to do this because not all App configuration policies apply to managed devices (more on this later). So let's sign into Intune, go under Users, and click New user.
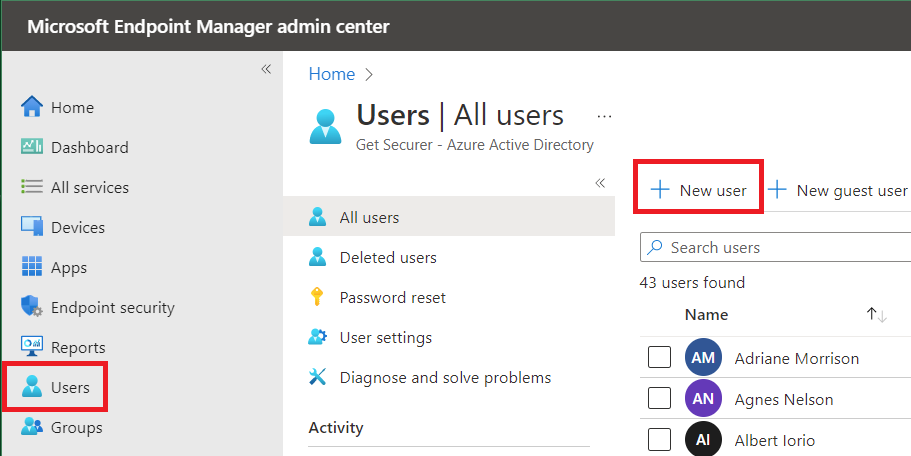
On the next screen, provide a user name, display name, set an initial password, set the usage location, and then click Create.
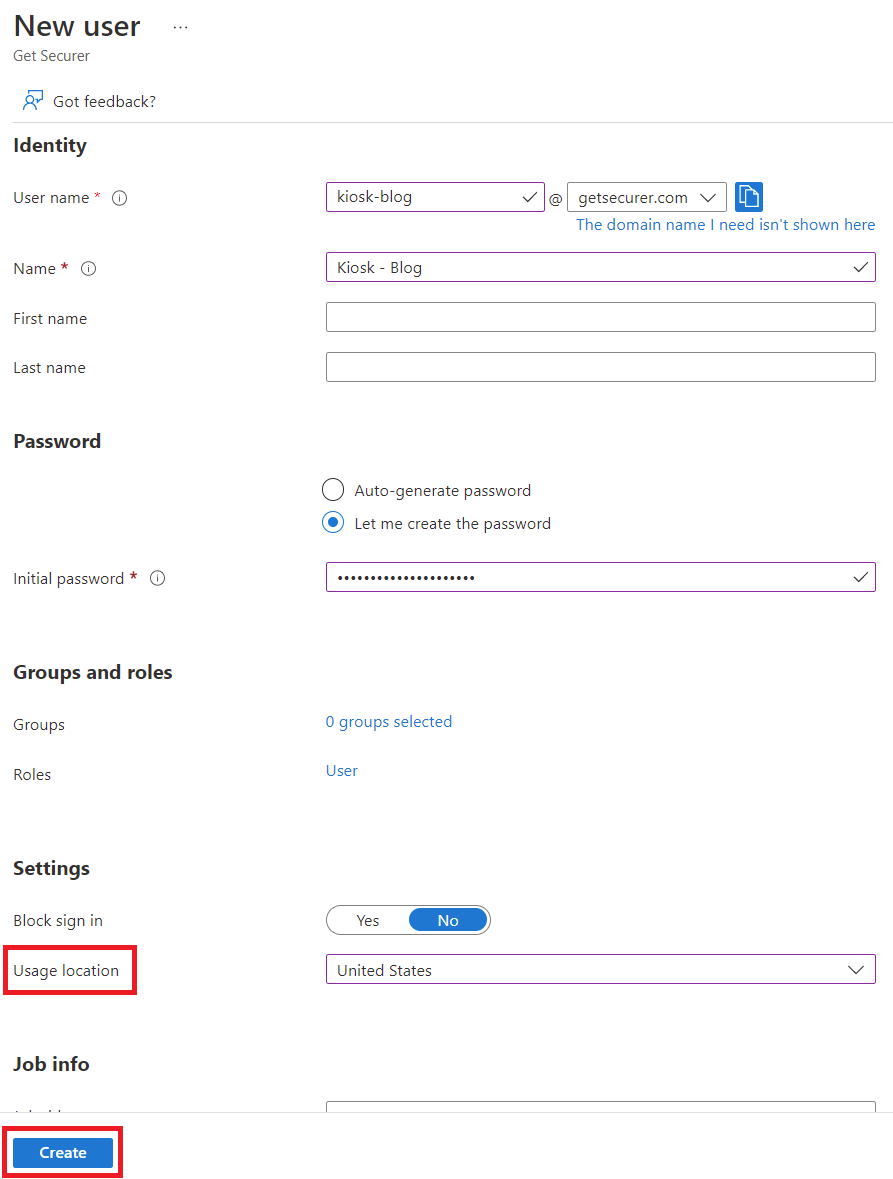
Once finished, we provision the kiosk iPad and sign in with our kiosk user.
Create Security Groups
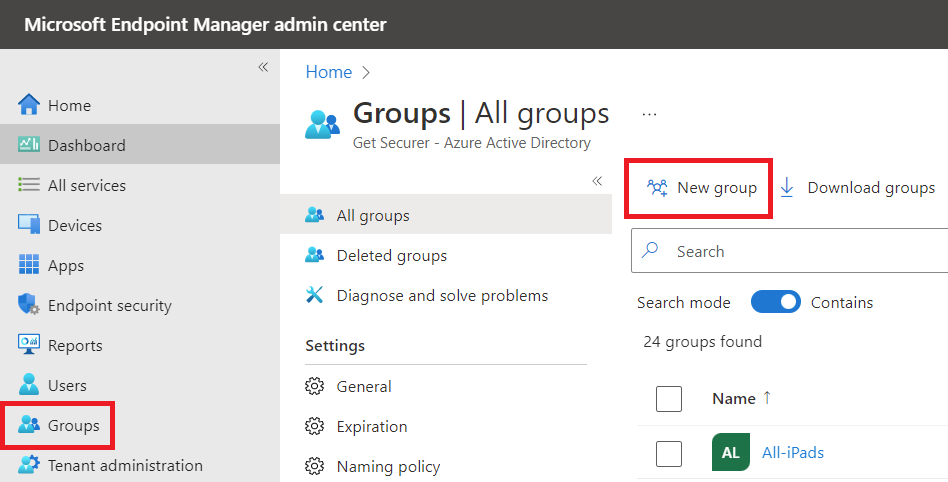
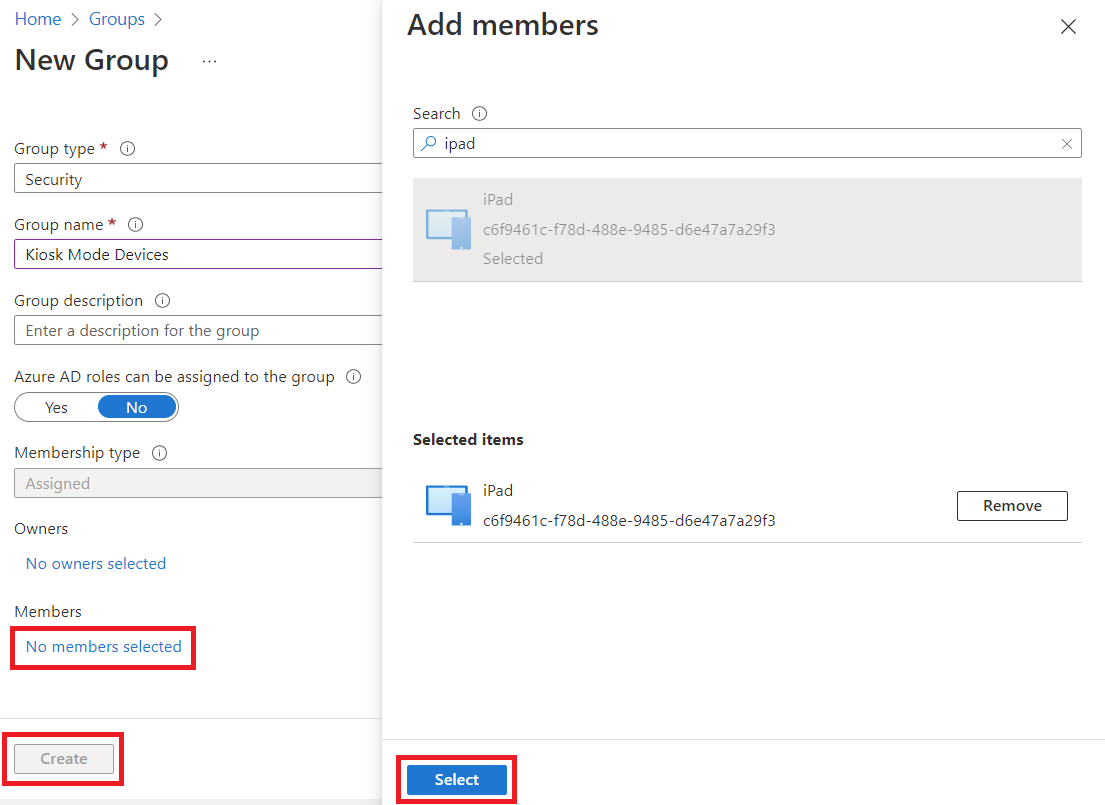
Next, create two security groups - one for the kiosk user and one for the kiosk devices. In Intune, go under Groups, then click on New group.
Give the group a name that will help you remember what it is used for (🤪), click on "No members selected", add the kiosk user, click Select, then click Create.
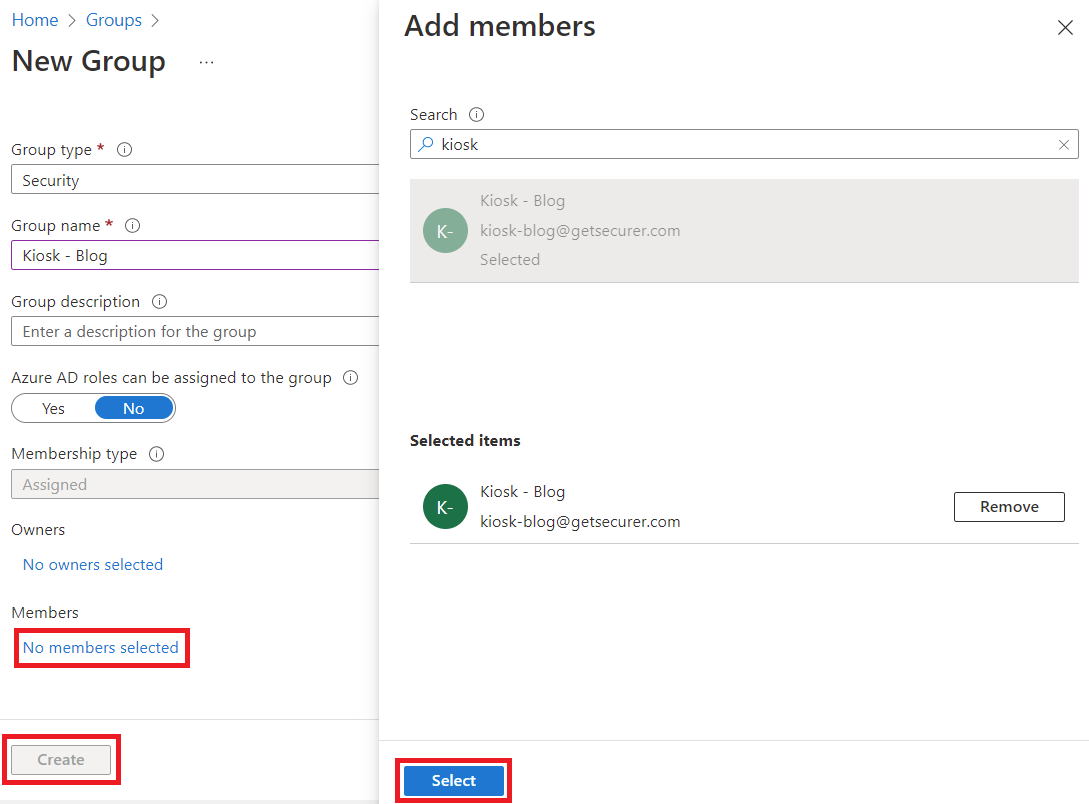
Now do the same to create the device group, add a test device (I always recommend starting with one test device), click Select, then click Create.
Deploy Edge
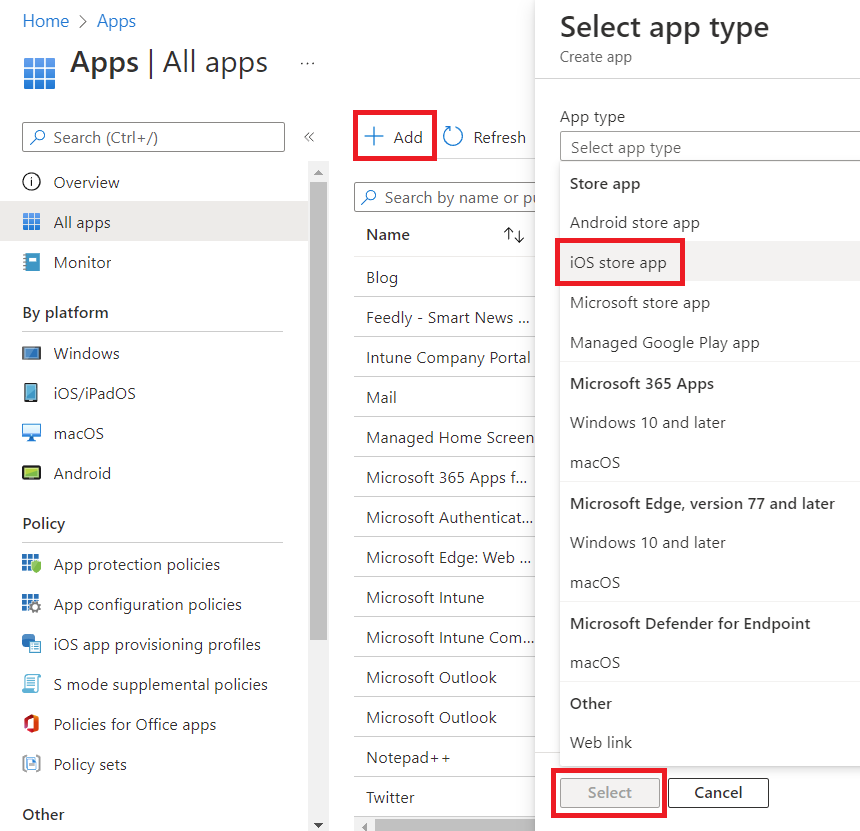
Next, navigate over to Apps, All apps, click Add, and select iOS store app.
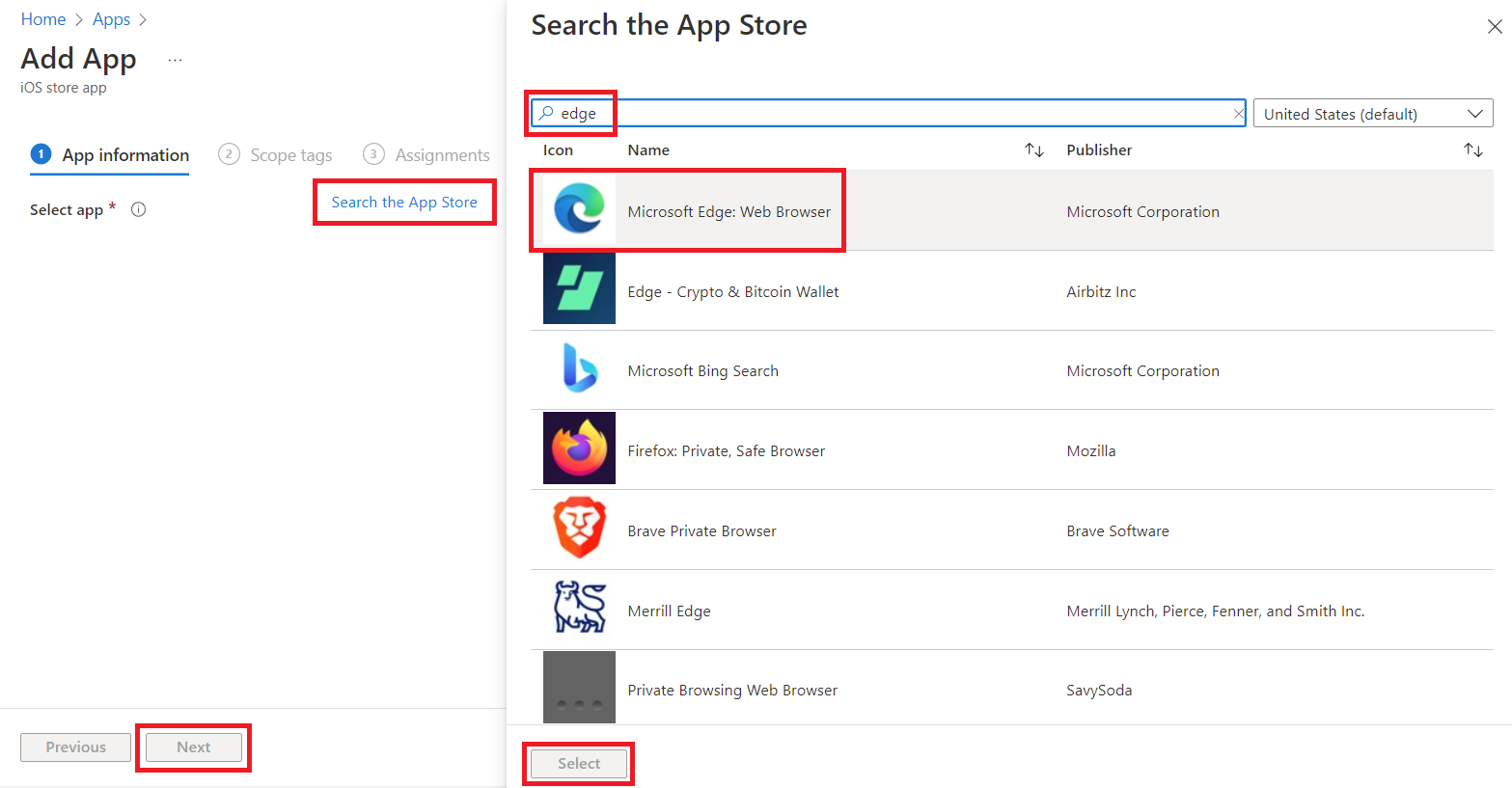
Click on Search the App Store, search for Edge, click Microsoft Edge: Web Browser, click Select, review settings you might want to change, then click Next.
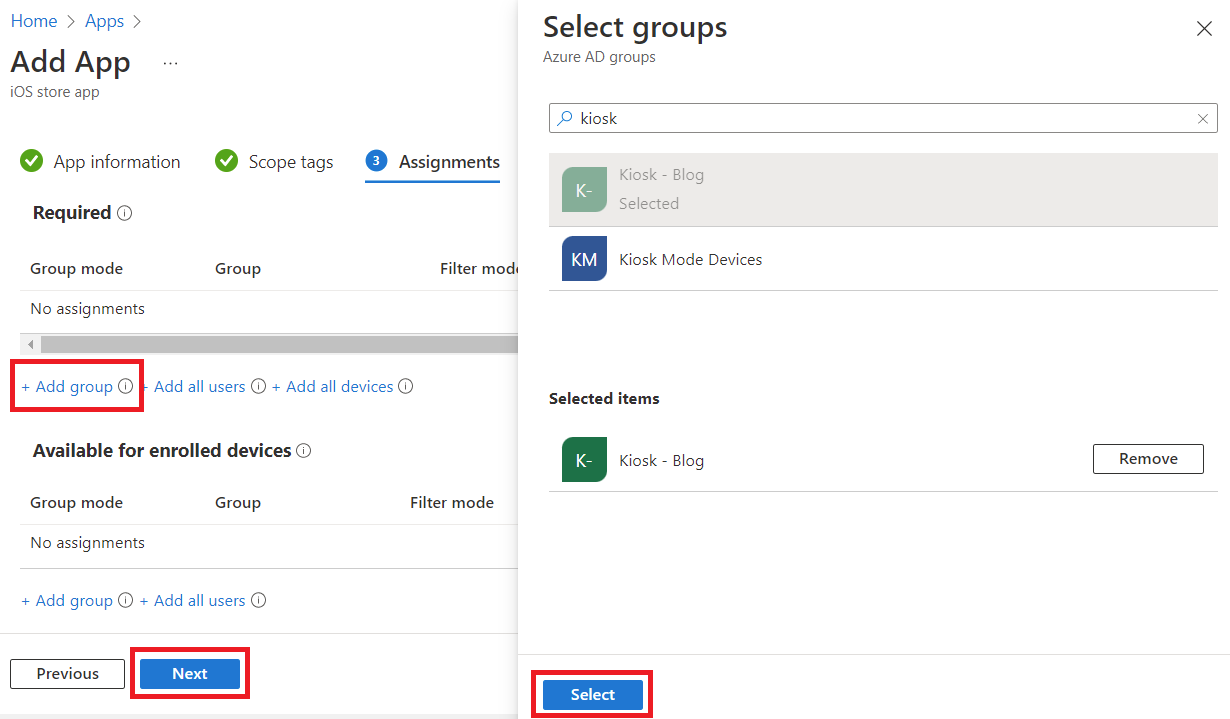
If you are using any scope tags, go ahead and select those as necessary, then click Next. On the Assignments tab, click Add group, search for your kiosk group, click it to add to the selected items, then click Select, and finally, click Next. Review the summary, and click Create when ready.
Create Application Configuration Profiles for Edge
Next, in the Apps section of Intune, scroll down under Policy and click App configuration policies. Click Add and select Managed apps from the dropdown.
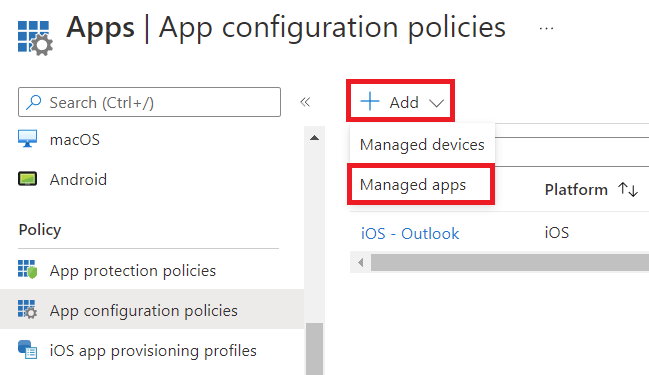
Provide a name for the policy, click Select public apps, click Microsoft Edge for iOS/iPadOS from the list, click Select, then click Next.
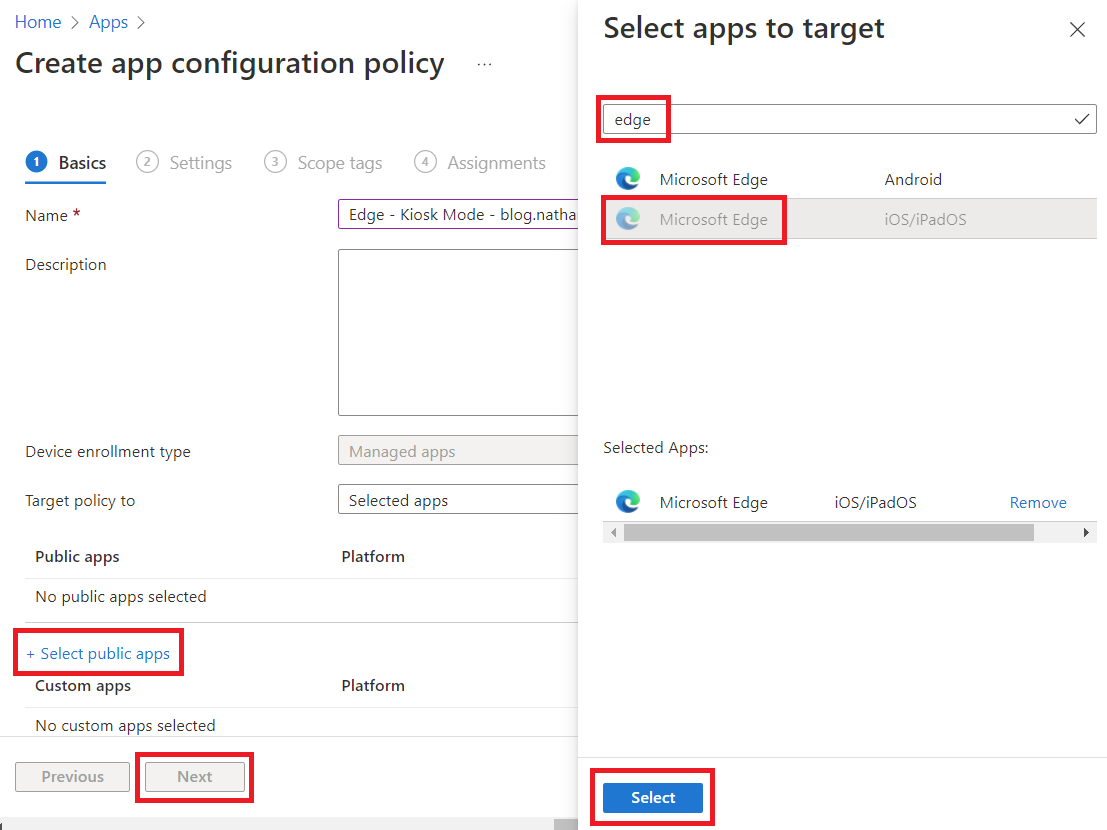
Edge is one of a few special apps that have pre-built policy definitions. Expand Edge configuration settings, then use Allowed URLs to limit browsing and Disable Redirect restricted sites to personal context. Be careful to include /* in allowed URLs if you want the full site to be accessible.
You'll also notice that we can integrate with Azure Application Proxy if needed. For more details on Edge policies, check out the docs over here: Manage Edge for iOS and Android with Intune | Microsoft Docs
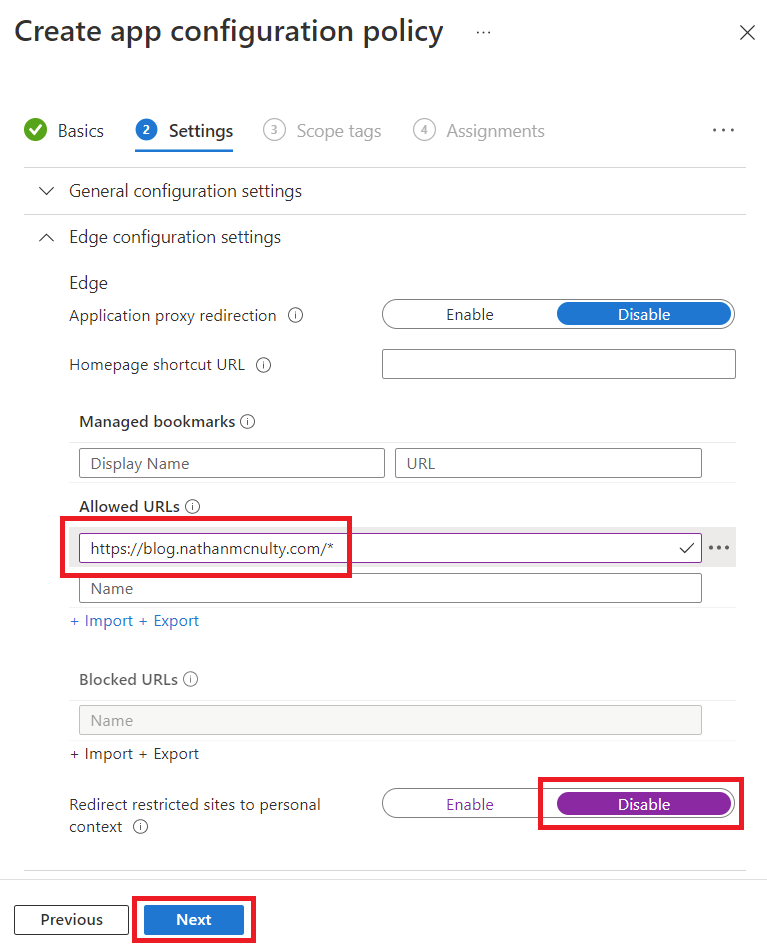
Click Next on the Settings tab when finished, click Next on Scope tags, then assign to our Kiosk security group, click Next, then Review and click Create.
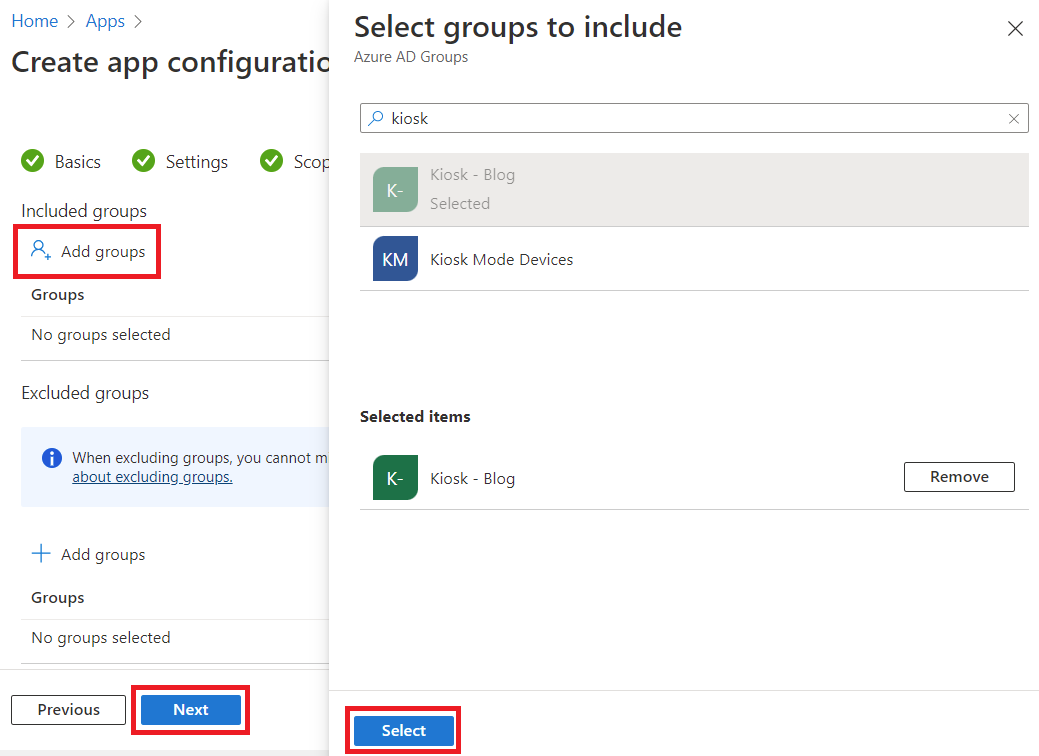
Now, we need to configure the Application configuration profile for the device as this is what allows us to set the new tab experience and force our kiosk user so the policies apply the way we need. Still in the Application configuration profiles section, click Add and select Managed devices from the dropdown.
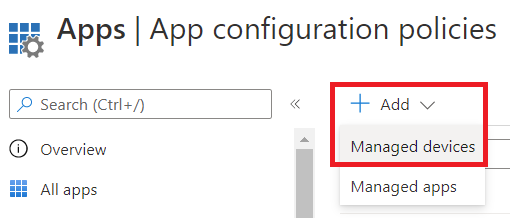
Provide a name for the policy, click Select app, select Edge from the list, click OK, then click Next.
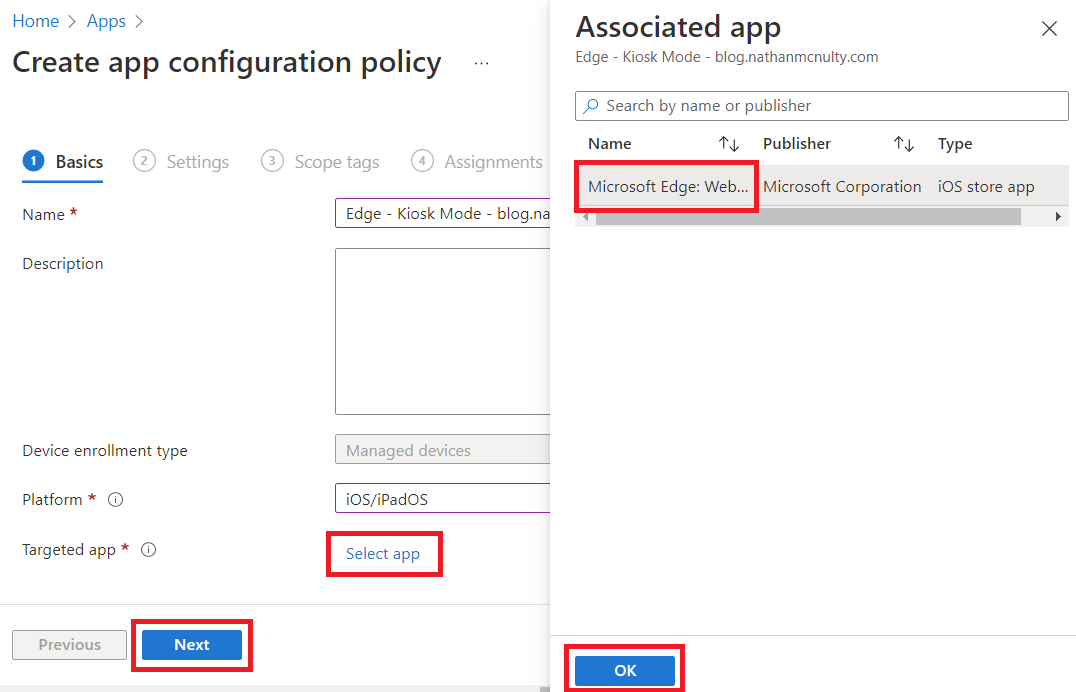
On the next screen, select Use configuration designer from the drop down.
Now we will enter the following keys:
IntuneMAMAllowedAccountsOnly
IntuneMAMUPN
IntuneMAMRequireAccounts
com.microsoft.intune.mam.managedbrowser.NewTabPage.CustomURL
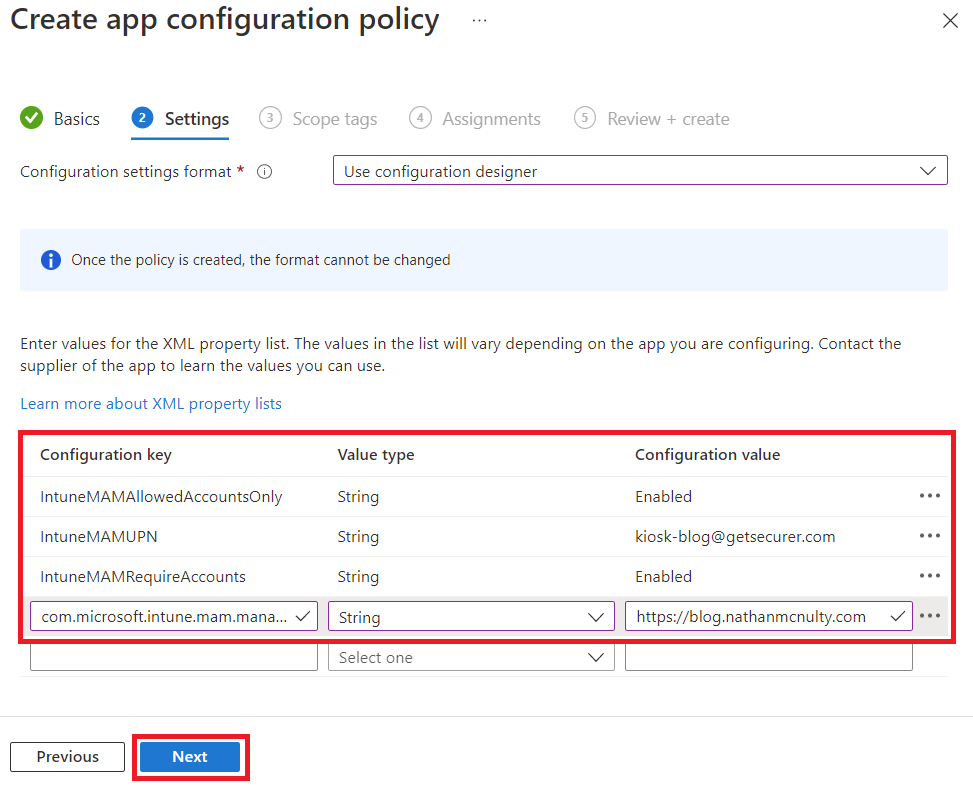
IntuneMAMAllowedAccountsOnly set to Enabled prevents personal accounts from being used. IntuneMAMUPN allows us to specify which account is should be signed into Edge. IntuneMAMRequireAccounts allows us to require the user specified by IntuneMAMUPN to sign in.
com.microsoft.intune.mam.managedbrowser.NewTabPage.CustomURL is the magical value that lets us override the new tab window with our web app!
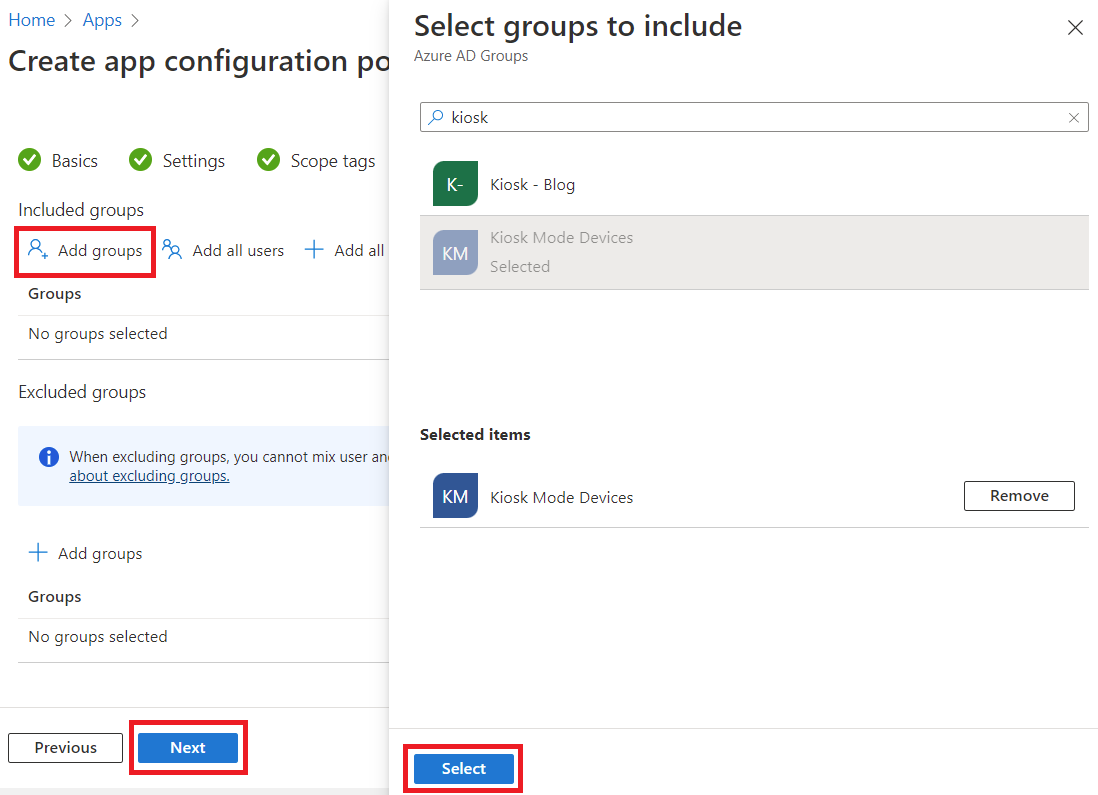
Click Next when finished, set scope tags if you use them, click Next, assign the policy to our devices group, then click Next, then review and Create the policy.
Create Configuration Profile for Kiosk Mode
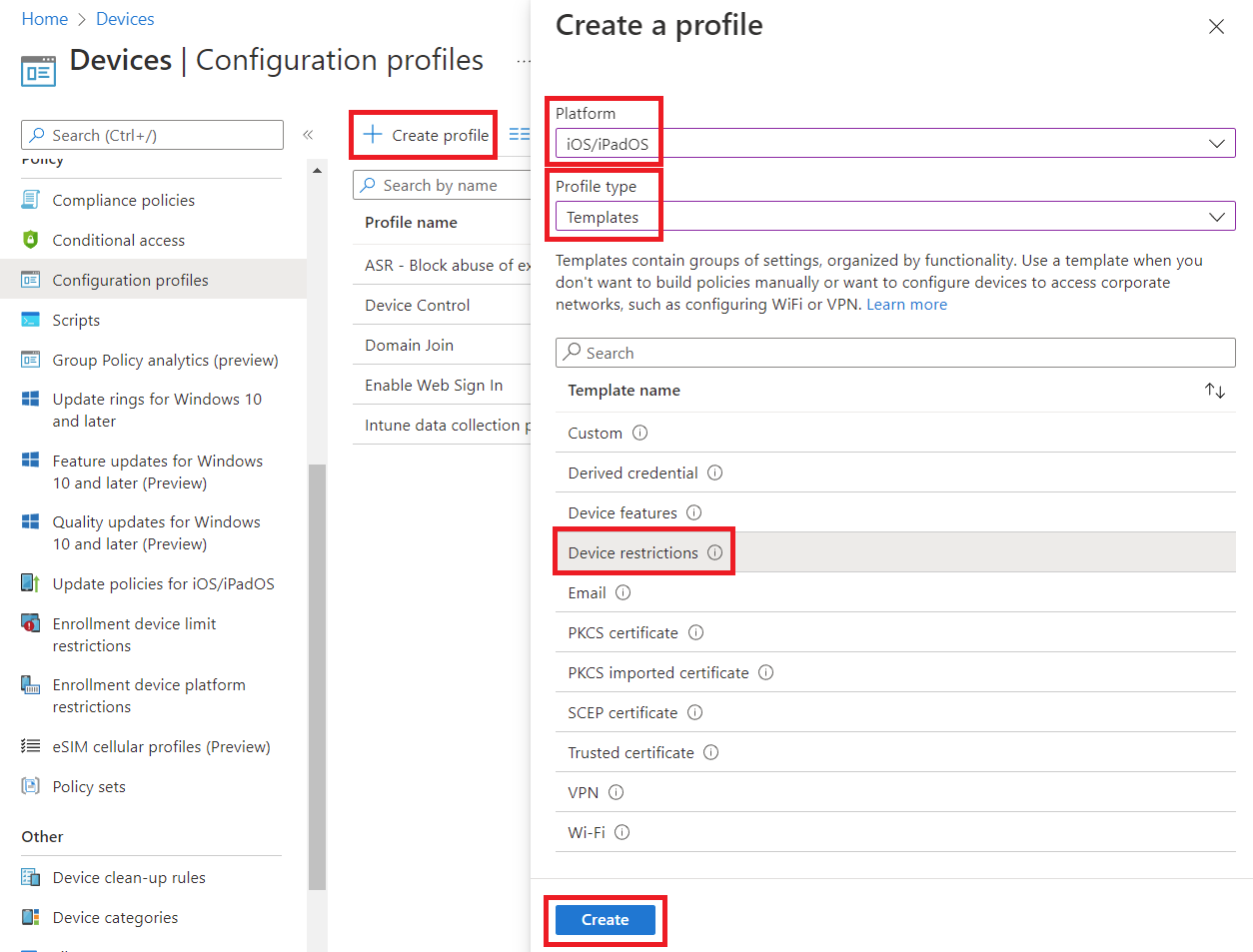
For the final step, navigate to Devices, scroll down and click on Configuration profiles, click Create profile, select iOS/iPadOS from the Platform dropdown, then select Templates from the Profile type dropdown. Under Template Name, select Device restrictions, then click Create.
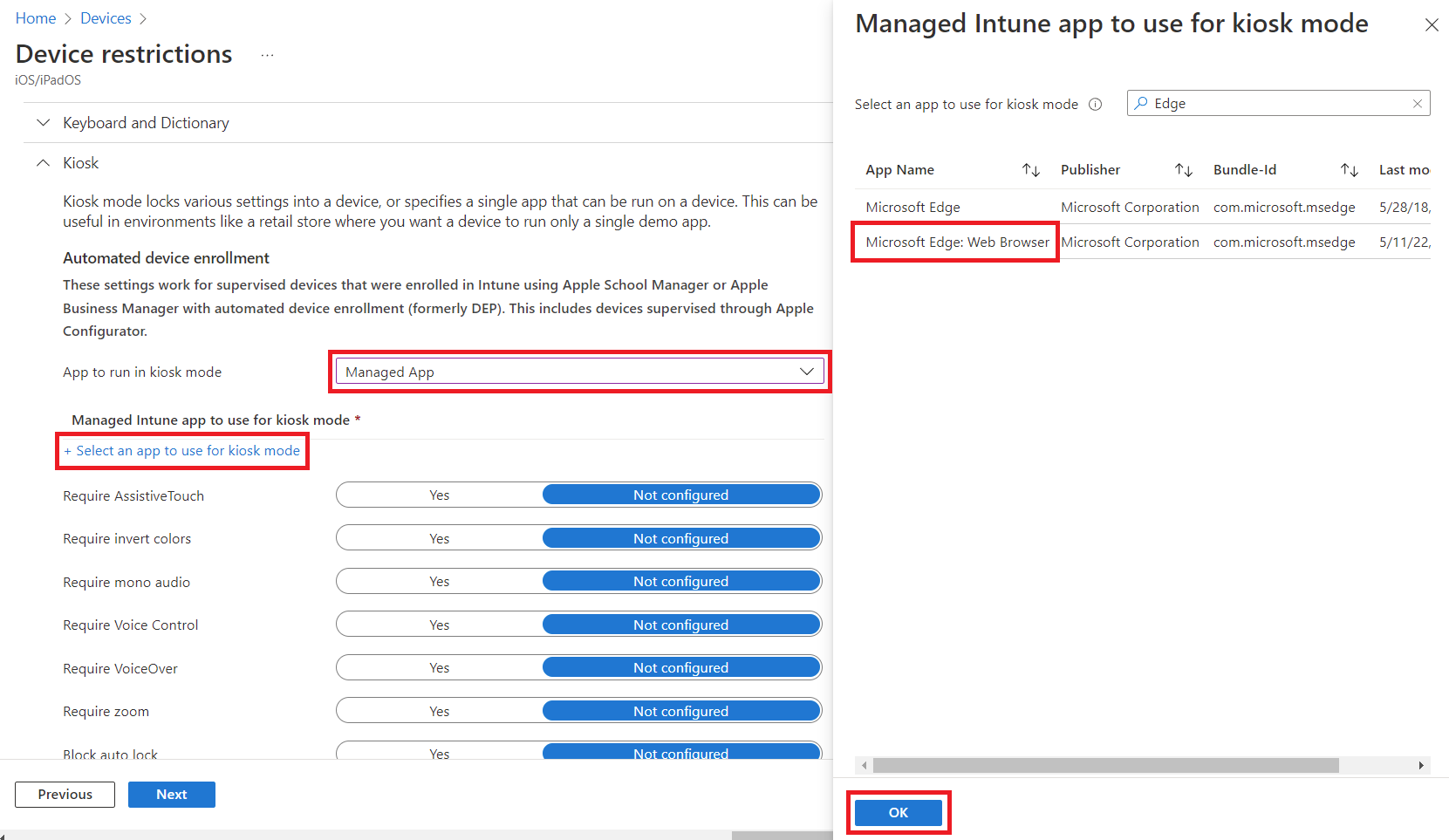
Provide a name and description, then click Next. On the Configuration settings tab, scroll down to the Kiosk category and expand it. In the App to run in kiosk mode dropdown menu, select Managed App, then click Select an app to use for kiosk mode. Search for Edge, click Microsoft Edge: Web Browser, then click OK.
If you have accessibility needs or other requirements, select those, then click Next
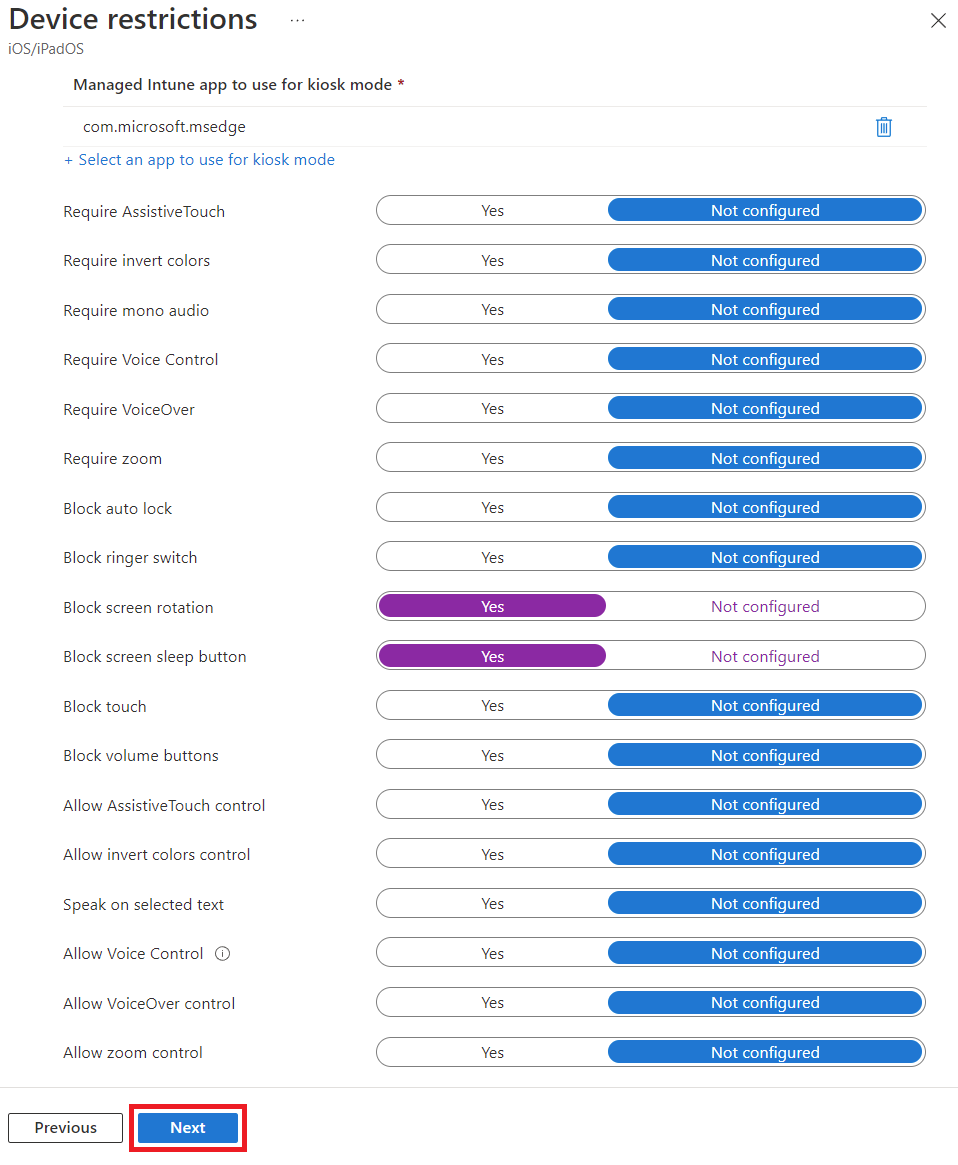
Select your scope tags if needed, then click Next. On the Assignments tab, click Add groups, search for your Kiosk group, click it in the list to add to the Selected items, then click Select. Finally, click Next, then review and click Create.
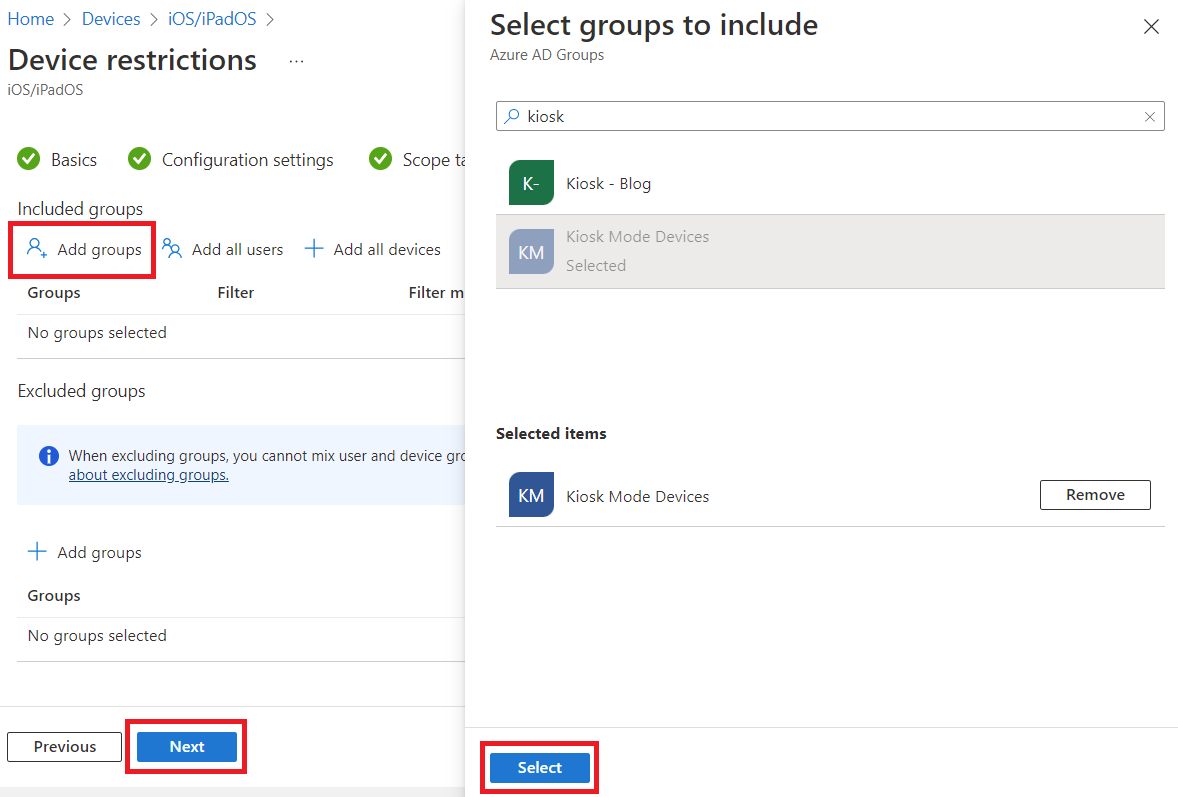
Within a few minutes, your device should launch Edge, sign in as your kiosk user, and display your web app. At this point, you should verify the app works correctly (navigate and test all the features) and verify you can't browse to other sites, exit the browser, etc.
Hopefully this was helpful, and if you find any errors, hit me up on Twitter ;)
