Defender for Endpoint - Removable Storage Access Control

Who wants to play with Defender for Endpoint's Removable Storage Access Control?
Yeah, me neither, but I'm doing it anyway
So what is it?
Well, it lets us do things like block writing to all removable media except specific ones using serial numbers
Microsoft Defender for Endpoint Device Control Removable Storage Access Control, removable storage media | Microsoft Docs
If you try to read the docs.. I apologize for the aneurism. They're pretty rough, but we'll get through it.
First, we need serial numbers for all our USB drives we want to allow 😬
"Hey Bob, here's an 8 step process to get serial numbers for me. No, you don't have to press F12" OK, so this could be done in a lot of ways, but the key is this:
(Get-PnpDevice -Class DiskDrive).PNPDeviceID | Where-Object { $_ -like "USBSTOR*" }
Since I have Intune, I'm going to use Proactive Remediation, so over to endpoint.microsoft.com to Endpoint Analytics we go :)
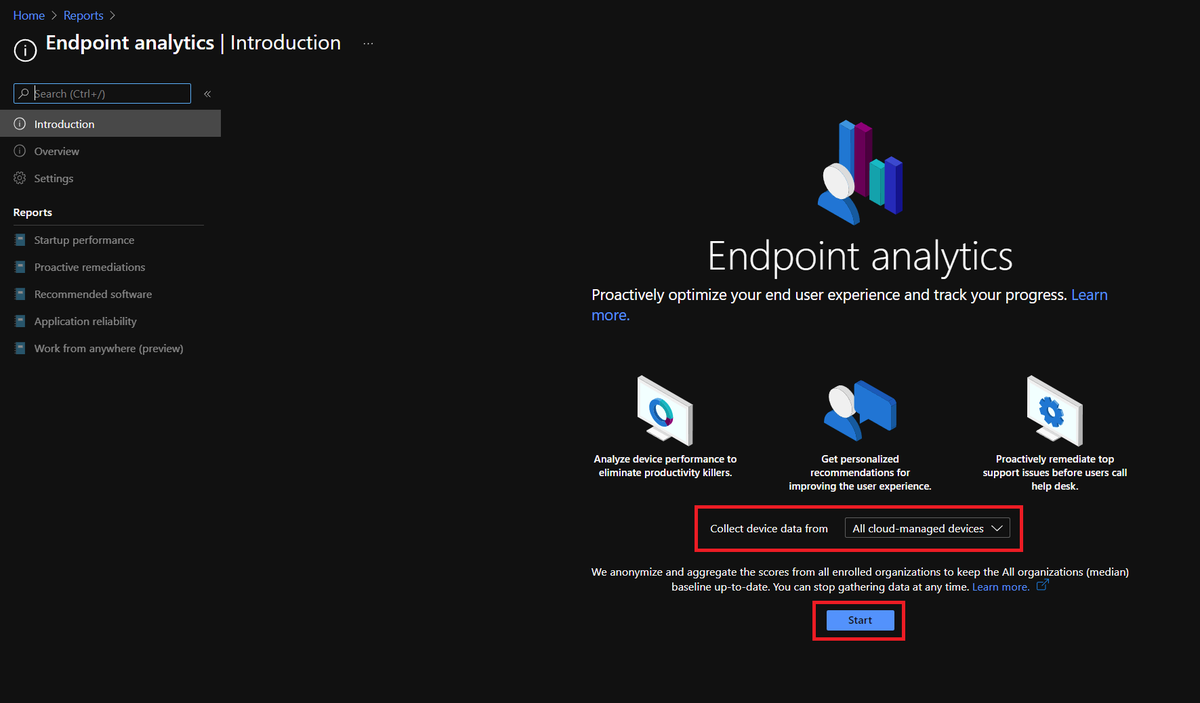
Now, if you've never used Endpoint Analytics, you might be presented with something like this
Just double check your licensing before enabling. Alternatively, this can be done with CI/Baselines in ConfigMgr or even Powershell writing to a file share.
Click Start and wait :P
OK, there are sooo many cool things in Endpoint Analytics. You owe it to yourself to read up on them:
What is Endpoint analytics? - Microsoft Endpoint Manager | Microsoft Docs
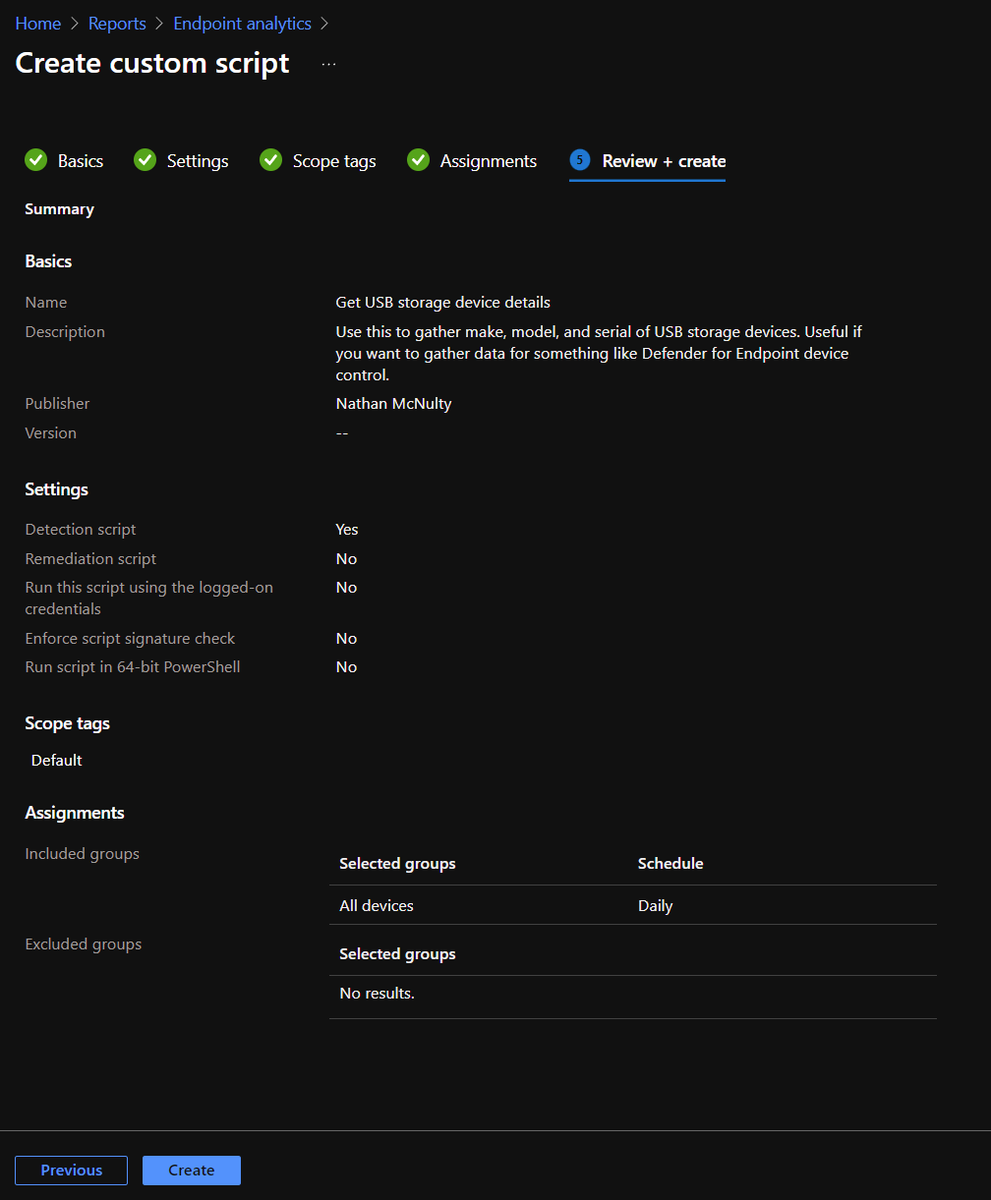
But today, let's go to Proactive Remediations, click Create script package, and create a custom script using the PowerShell command from earlier :)
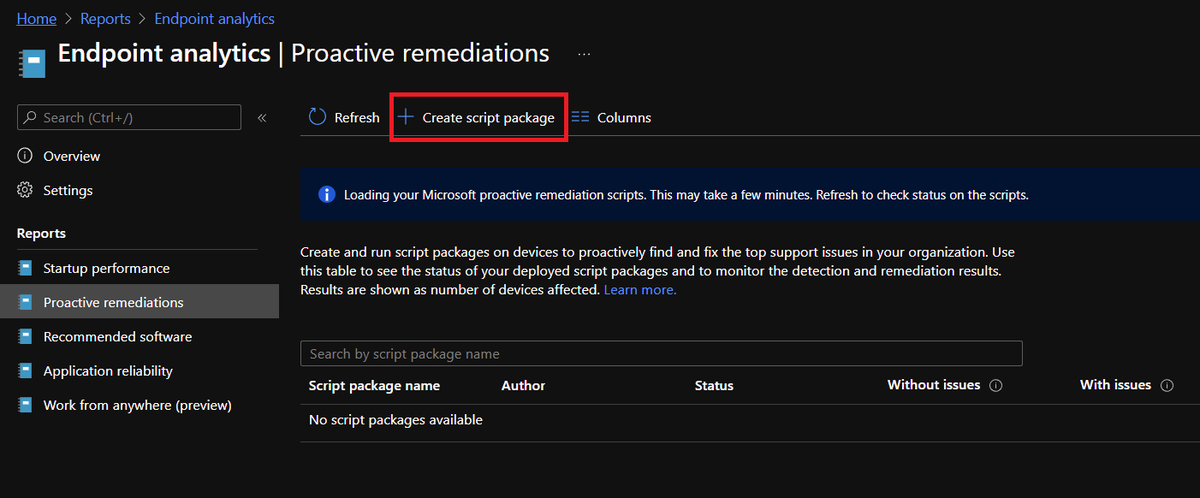
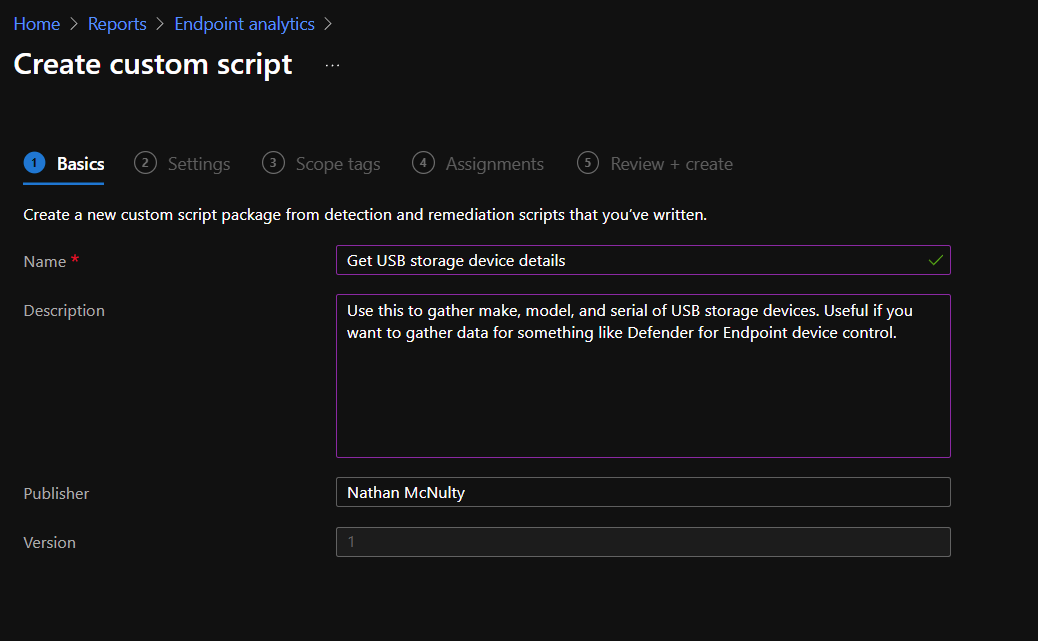
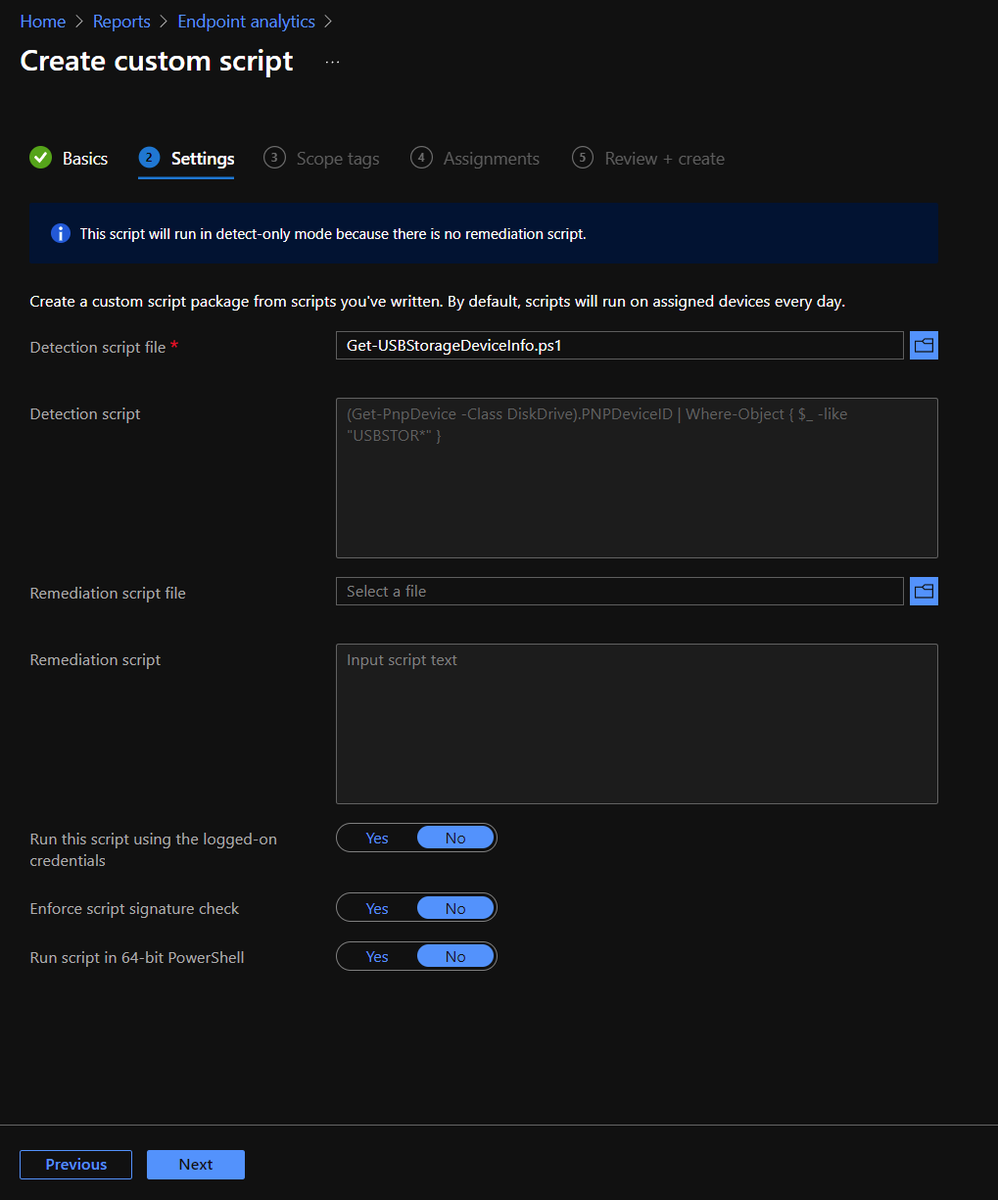
Now I collected from all devices and set to run daily. Scope and use settings as you feel are reasonable for your environment, but know this specific command is very low cost ;)
You should see success, and the clients will simply run this and submit the results back to Intune.
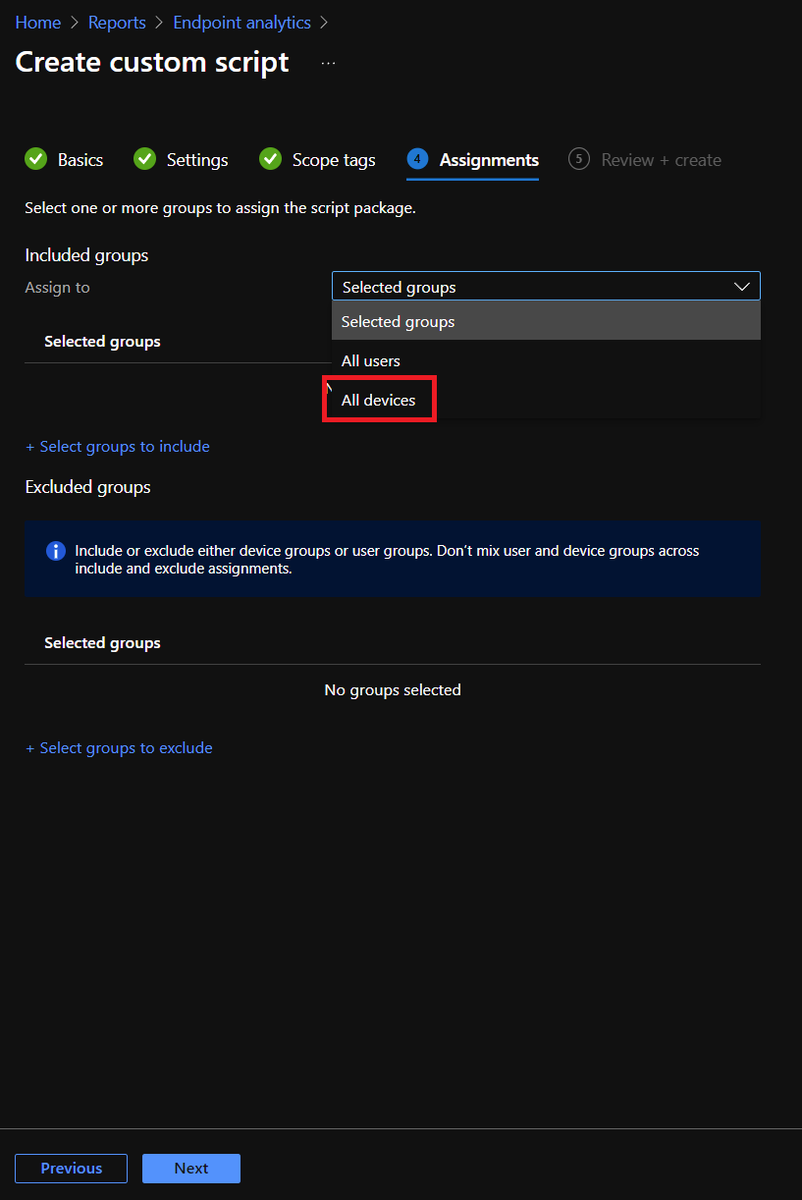
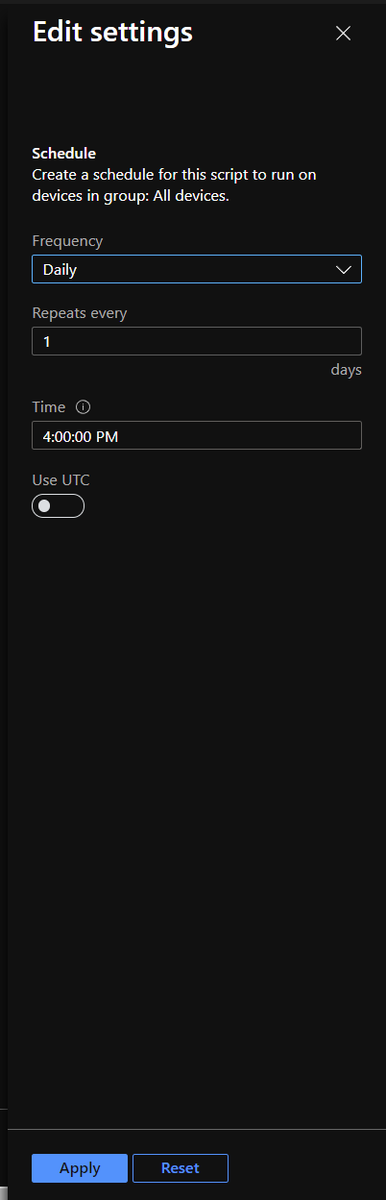
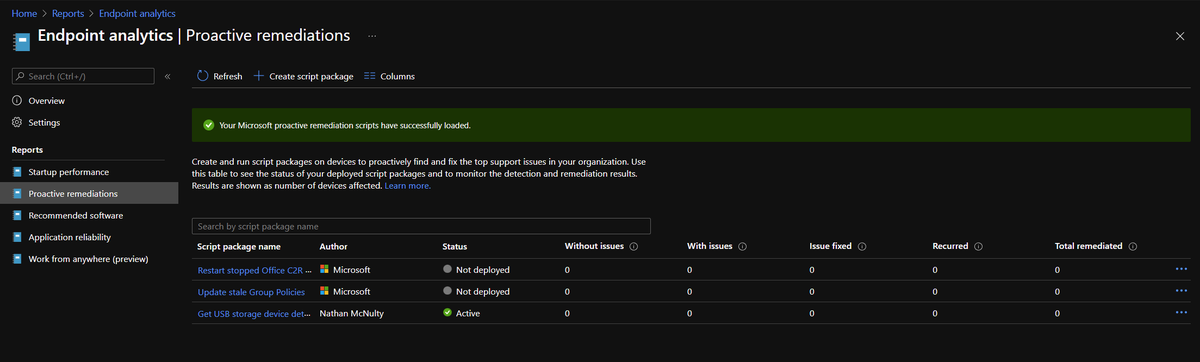
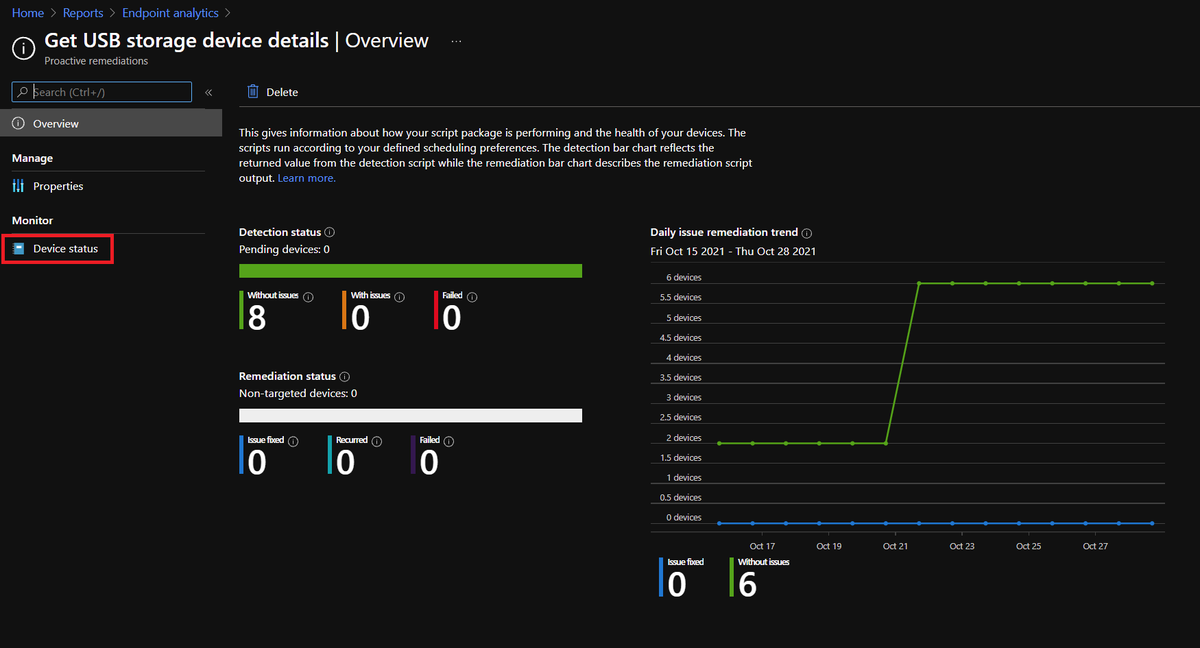
I love this method because we can export the data from Intune rather than writing to a storage blob / file share from the client like we used to have to do :)
Once we've waited long enough for data to come back, we go into our script package, click Device status, and Export!
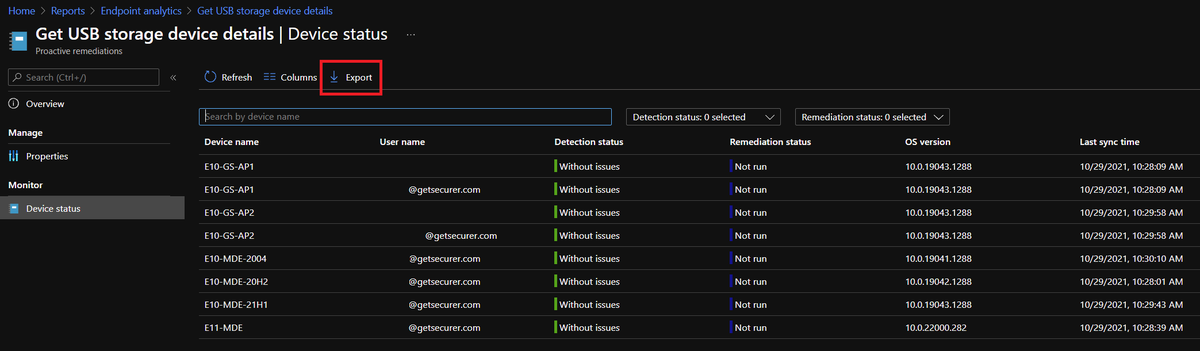
Cool, so we have data. Now how do we use it?
Well, we create groups and policies using XML files as shown here:
Microsoft Defender for Endpoint Device Control Removable Storage Access Control, removable storage media | Microsoft Docs
I grabbed the example XML files from their GitHub and modified them
mdatp-devicecontrol/Removable Storage Access Control Samples/Intune OMA-URI at main · microsoft/mdatp-devicecontrol (github.com)
These screenshots would be for Group Policy
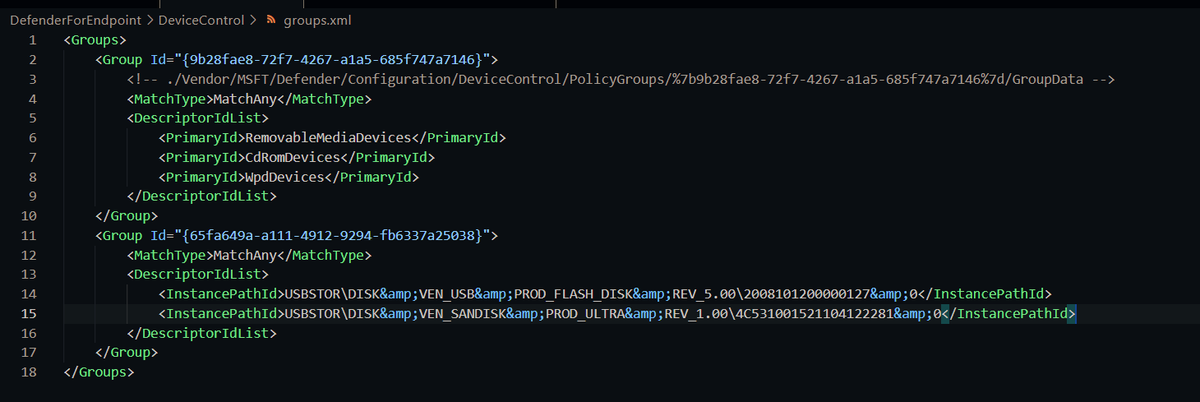
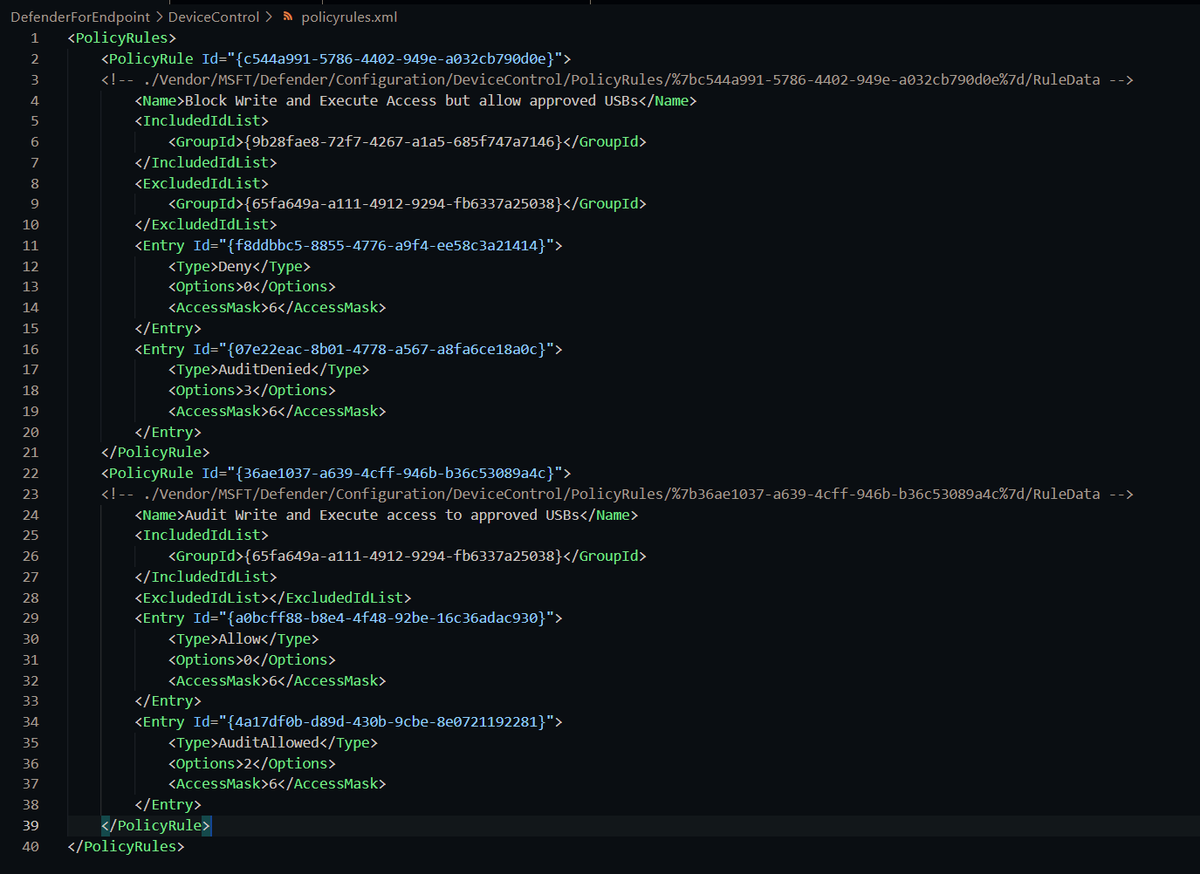
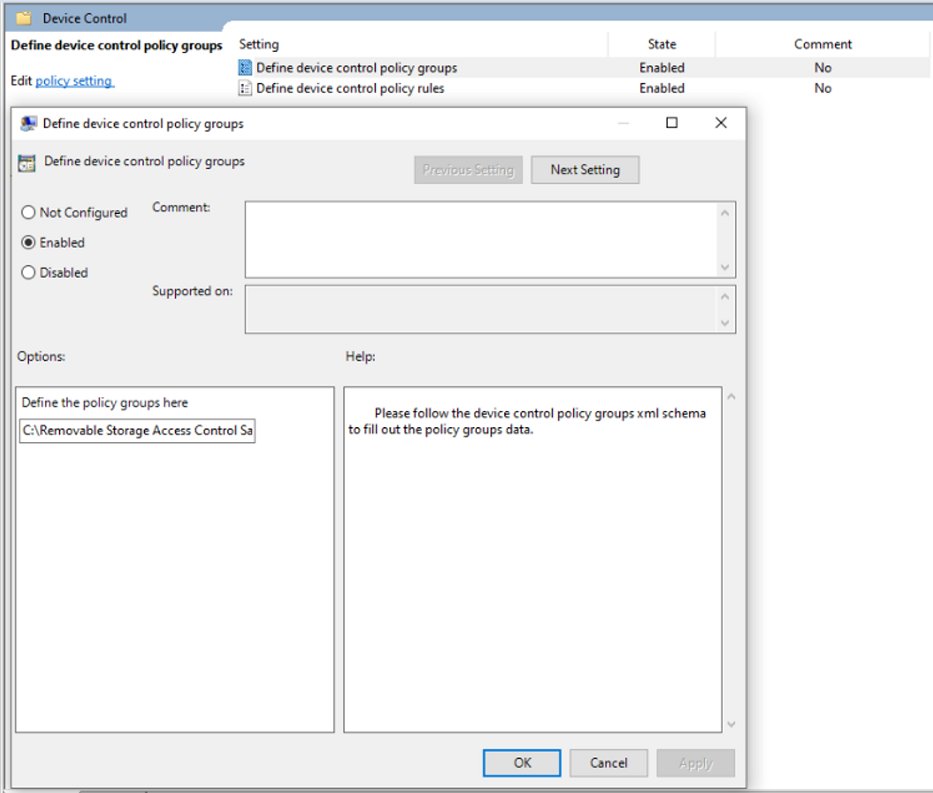
In Group Policy, we have to combine all our groups into one XML and policy rules into another XML
Groups allow us to specify device type and serial numbers
Policy rules define what we do with devices matching those groups
For Intune, each group/rule is a separate XML like this
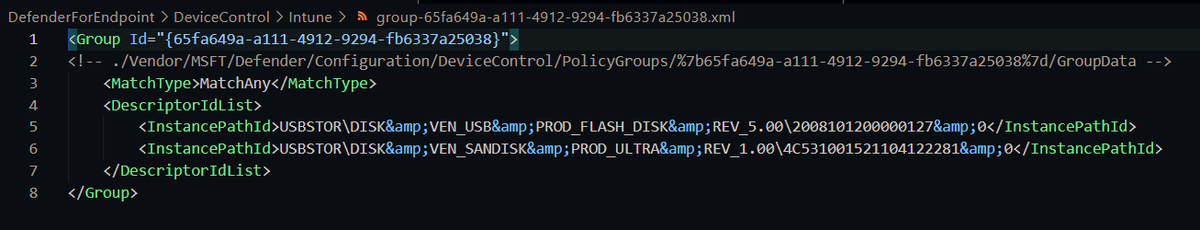
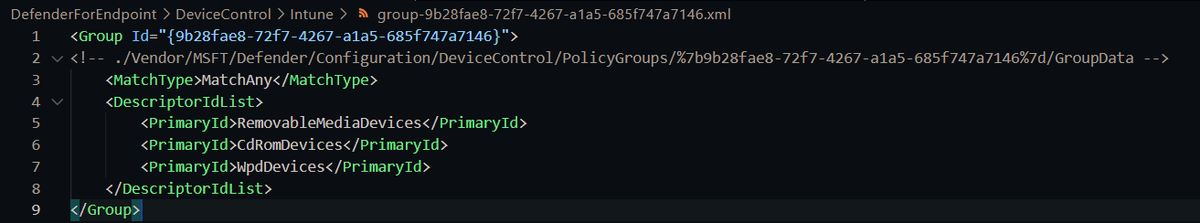
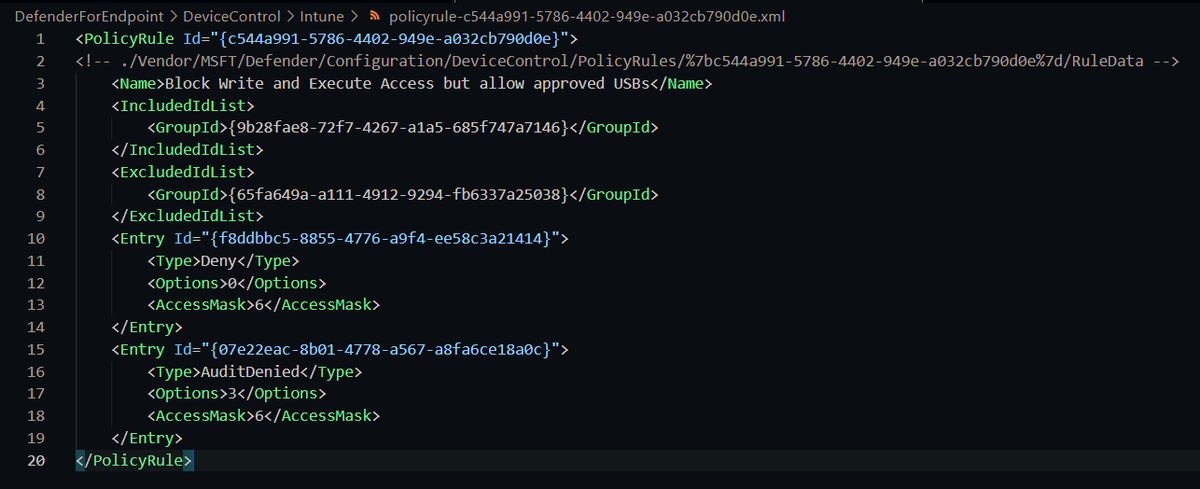
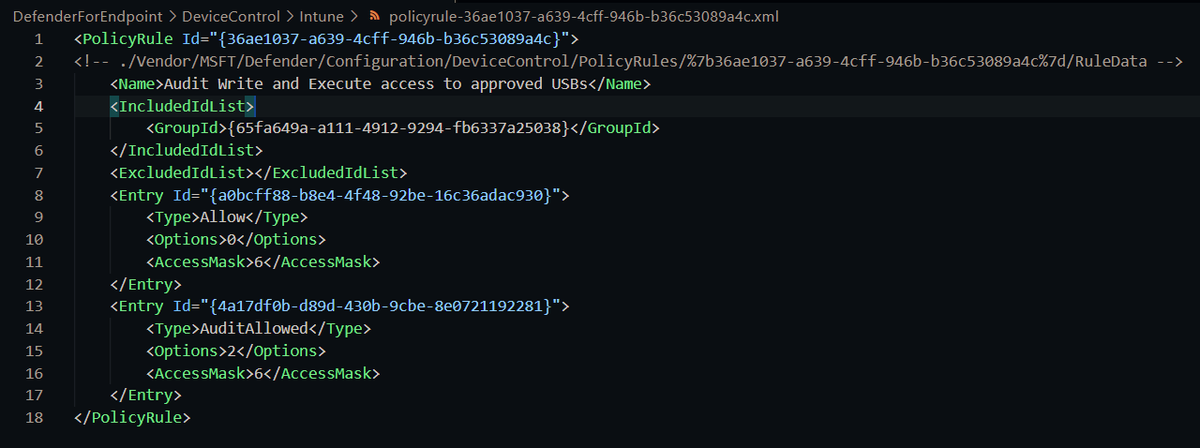
To help, I've put all these XML files here:
nathanmcnulty/DefenderForEndpoint/DeviceControl/Intune at master · nathanmcnulty/nathanmcnulty (github.com)
So let's create our Intune policy :)
In MEM admin center, we go to Devices - Windows - Configuration profiles and Create profile
This will be a Template profile type, select Custom template, and click Create
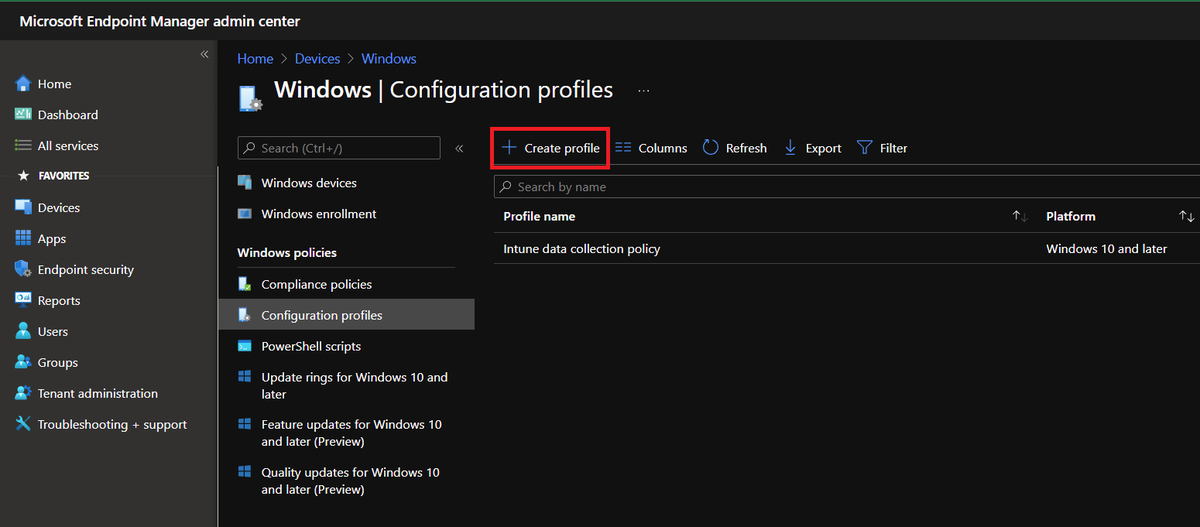
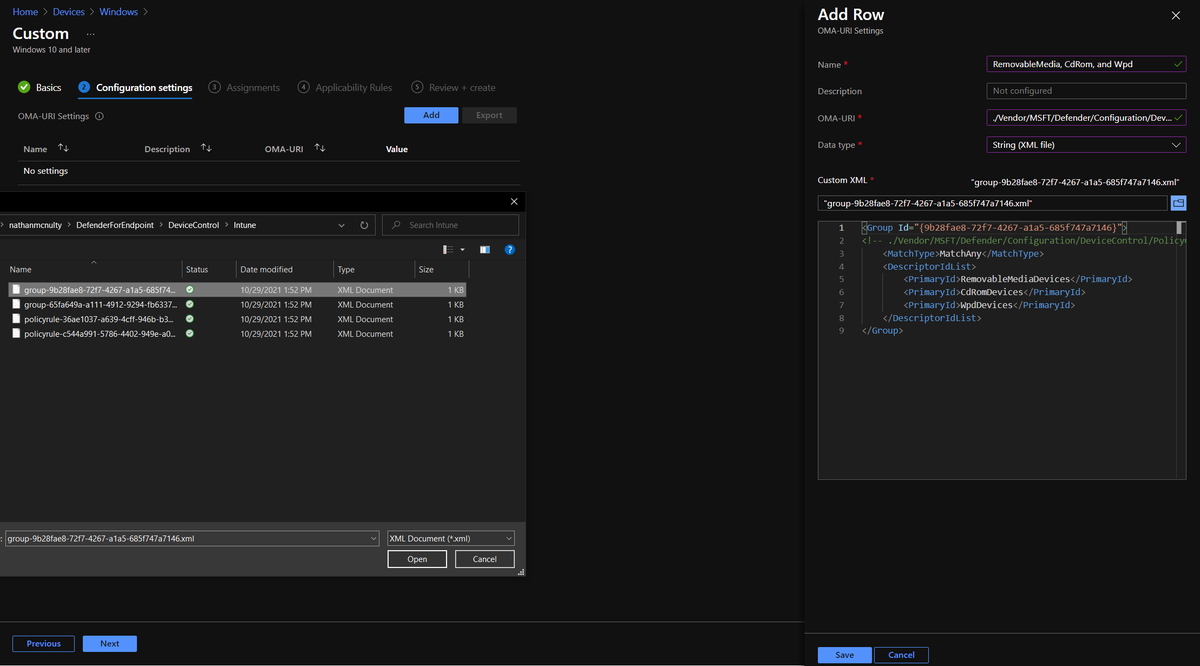
Give it a name, then add each group and policyrule as an individual OMA-URI setting
Sadly, you can't paste the content in - you have to save as XML...
NOTE: The OMA-URI field is unique to each one. GUID matches ID in XML (see the comment in the XML)
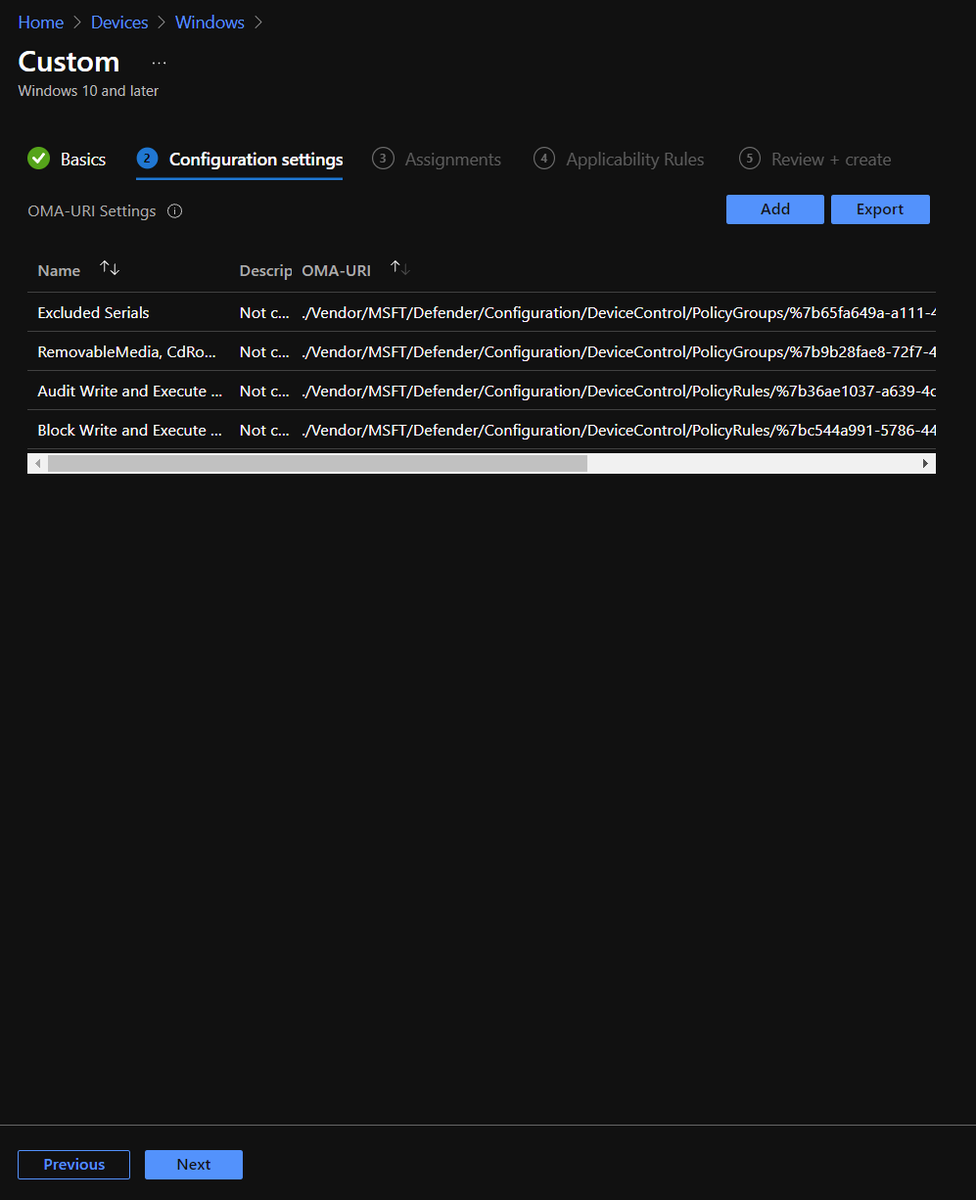
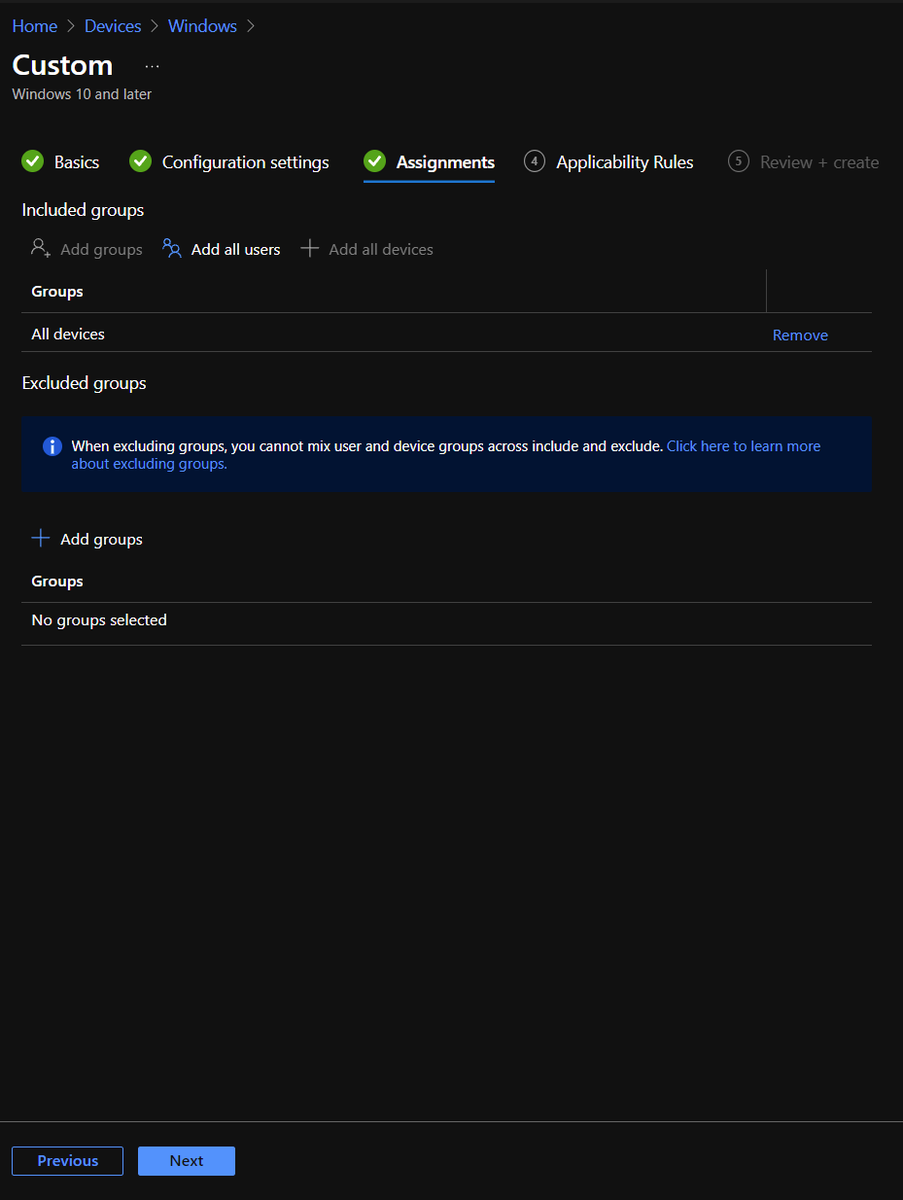
Now we assign the policy to the groups we want, assign applicability rules if you want, and create
Note on applicability rules - if a device has two conflicting rules, the one without applicability rules will win over the one that has them ;)
And now your devices should prevent write access to USB devices that are not explicitly allowed by policy
The docs state you can use an Attack surface reduction Device Control policy under Endpoint security in Intune, but I couldn't find anywhere to exclude devices, only block
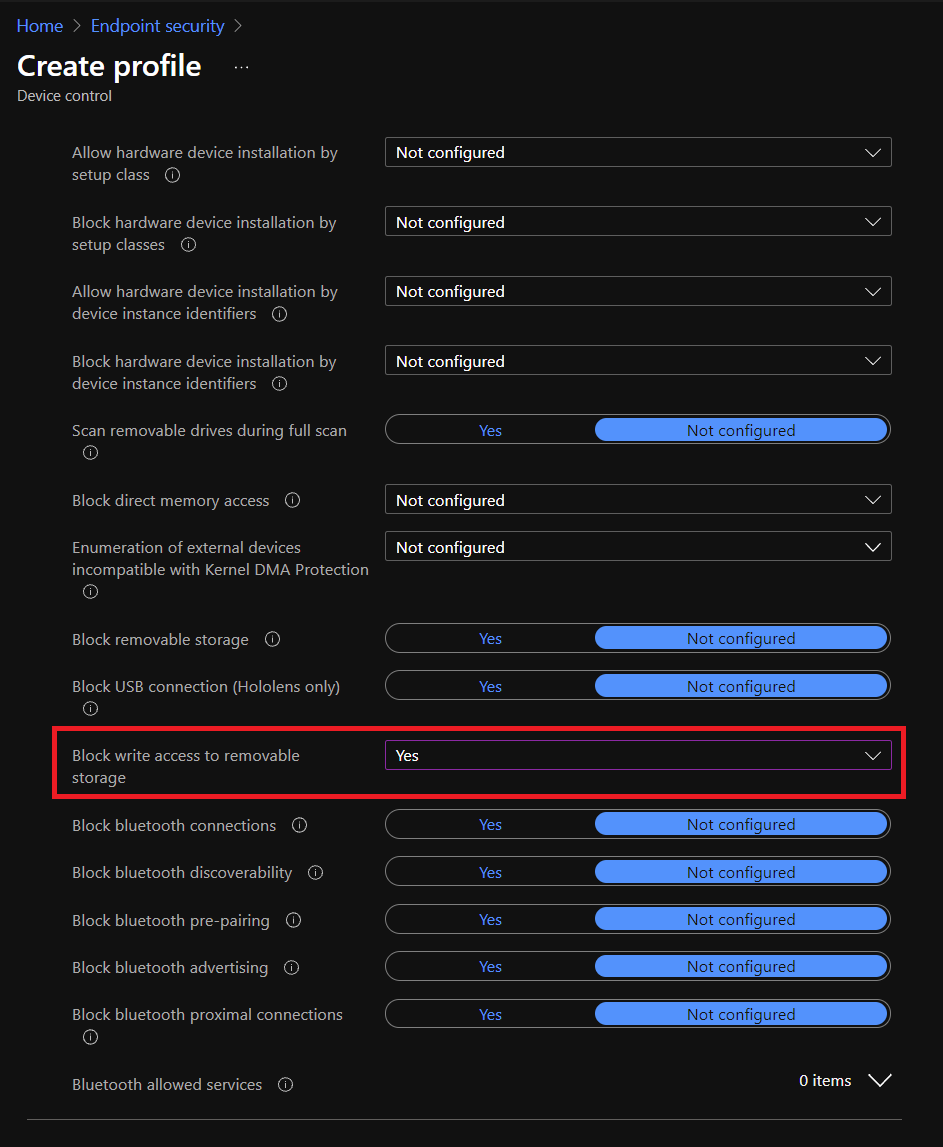
This was originally posted on Twitter, and you can find the discussion over here:
Who wants to play with Defender for Endpoint's Removable Storage Access Control?
— Nathan McNulty (@NathanMcNulty) October 29, 2021
Yeah, me neither, but I'm doing it anyway
So what is it?
Well, it lets us do things like block writing to all removable media except specific ones using serial numbershttps://t.co/5vLUZqyPOB pic.twitter.com/LtJ4vXCJ7e
