Azure - Securing Subscriptions

I recently shared a list of things I like to take a look at when adding Azure Subscriptions, and I'd encourage you to check out the Twitter thread for ideas from other folks as well. I'm adding this blog post simply to capture the content for preservation and future additions :)
What are some of the first things you do when setting up Azure subscriptions?
— Nathan McNulty (@NathanMcNulty) February 26, 2023
Here's some of my favorites, and I'd love to hear from others too :)
First, I always start by setting up billing anomaly alerts (and budgets/budget alerts)https://t.co/7qNPBxXiJJ pic.twitter.com/qS0ply93ZB
The goal of my post was to share some quick wins for any organization and have others share anything missing that would add value. Hopefully this is helpful to others out there, and as always, let me know if you have any comments or questions!
What are some of the first things you do when setting up Azure subscriptions? Here's some of my favorites, and I'd love to hear from others too :)
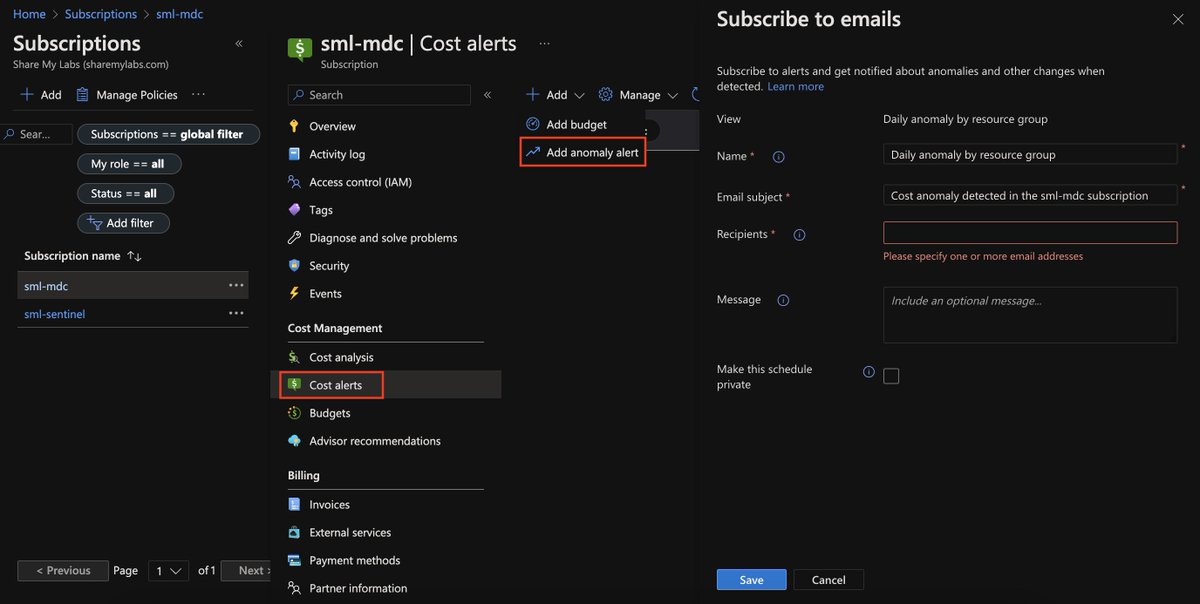
First, I always like to start by setting up billing anomaly alerts (and budgets/budget alerts): Identify anomalies and unexpected changes in cost - Microsoft Cost Management
This is free to set up and can save a ton of money if mistakes are made around scaling, automated deployments go wrong, or an attacker gains access and spins up a ton of resources.
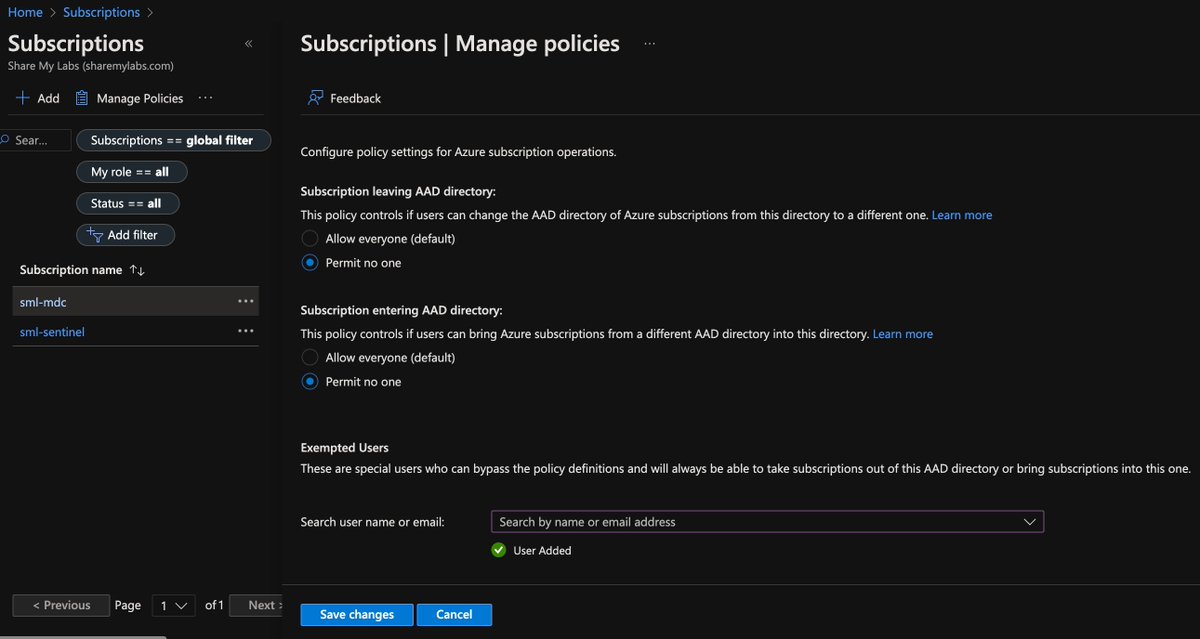
While I'm at it, I always double check to see who can transfer subscriptions in and out of my tenant. Attackers can transfer subscriptions to their own tenant but leave you with the billing, so you likely won't see resources being created and generating cost until it's too late.
It's best to disable both incoming and outgoing subscriptions and then only exempt administrative users when you actually need to perform these actions.
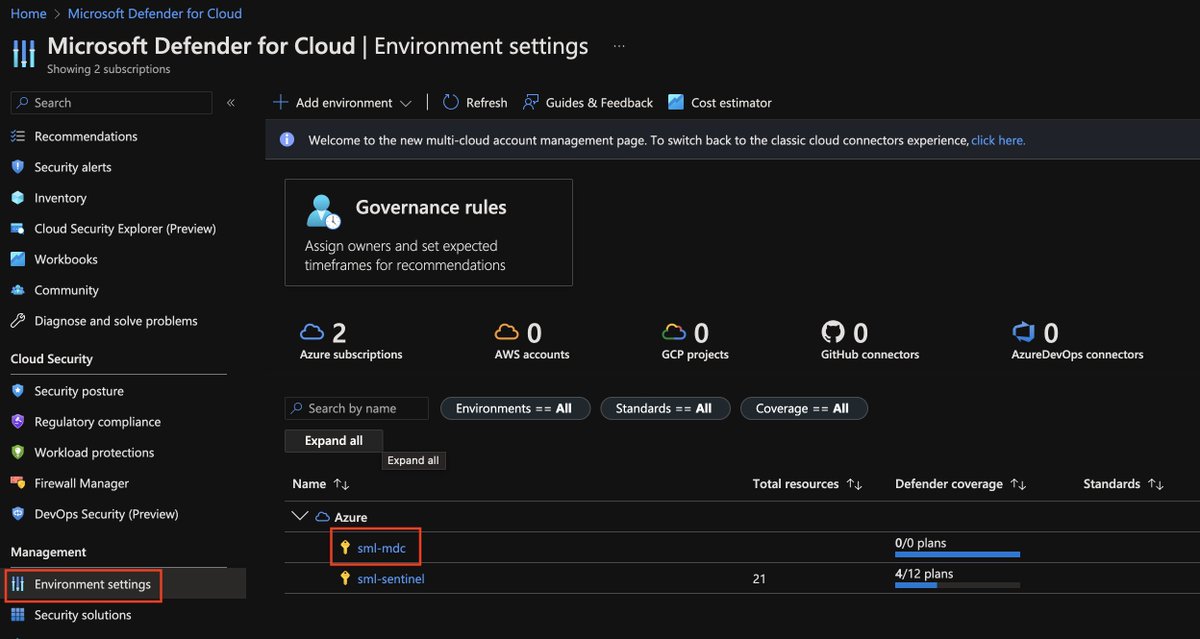
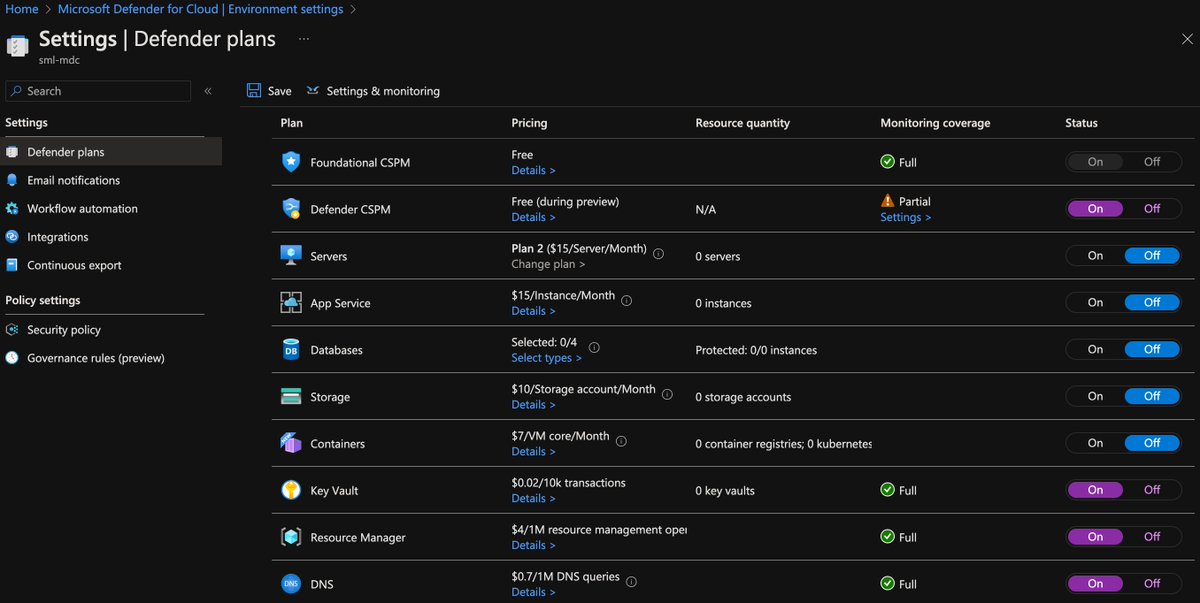
I have a few items in Defender for Cloud that I always enable - Key Vault, Resource Manager, and DNS. These three are very cheap insurance, and you can enable others as it fits your organization. You can also enable custom initiatives for security recommendations: Create custom Azure security policies in Microsoft Defender for Cloud
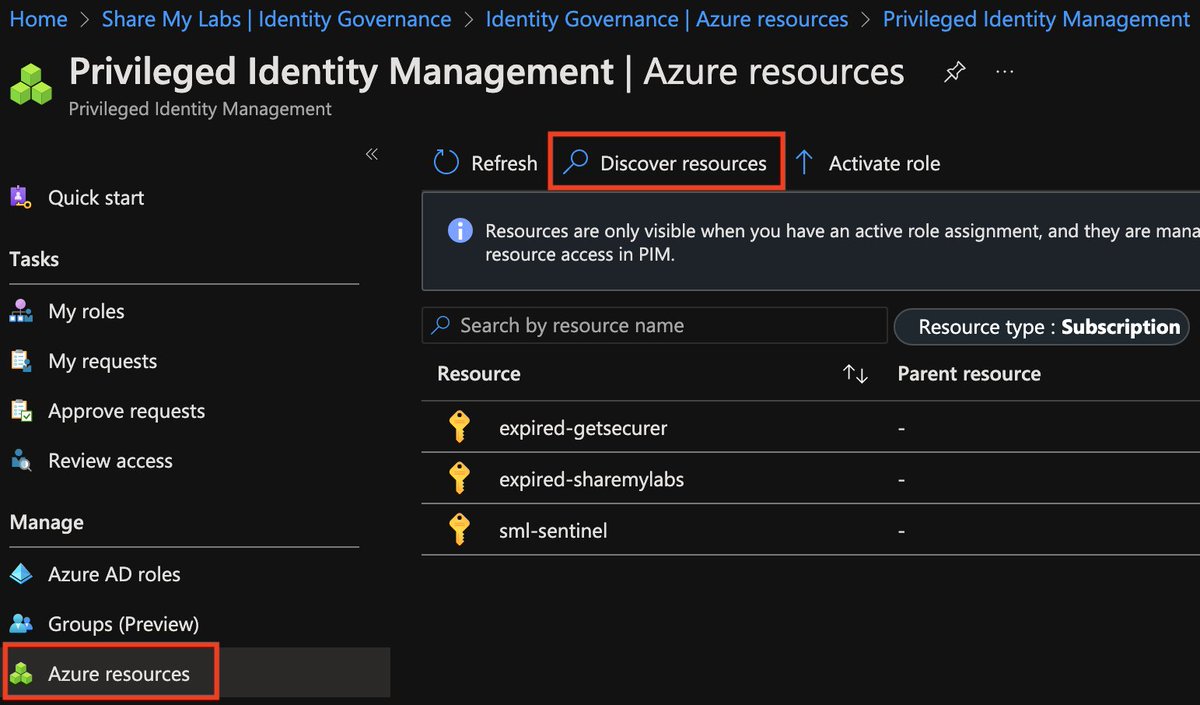
If I'm fortunate enough to have Azure AD P2 for my Azure admins/users, I always bring my Subscriptions into Privileged Identity Management: Discover Azure resources to manage in PIM - Azure AD - Microsoft Entra
This provides us with better controls and visibility of when admins are using privileges, and we can tie it into Access Reviews to ensure they are actually using the privileges we've given them.
I generally recommend starting with Owner, User Access Administrator, Contributor, and other easy wins like Key Vault Admins.
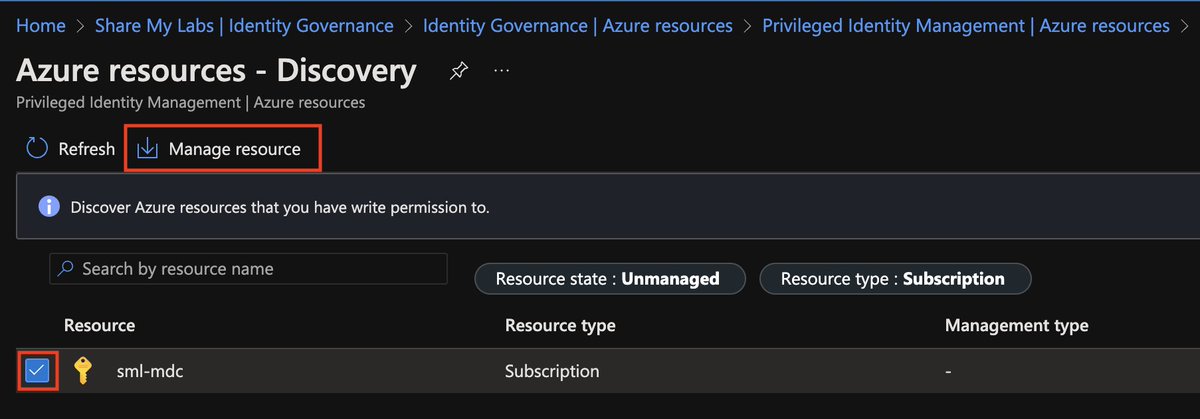
With Conditional Access, I may allow Reader role using any form of MFA, but for Owner / Contributor, I want really want to require stronger, phishing resistant authentication.
We can now do that by using Authentication contexts in PIM. @merill shared a great, concise guide here:
Question: What's better than peanut butter and jelly for an Azure AD admin?
— Merill Fernando (@merill) February 24, 2023
Answer: Our newly launched feature that adds conditional access policy support to Azure AD PIM.
Folks, this is a marriage made in heaven. Read on for a quick walkthrough. 🧵👇🏾 pic.twitter.com/wKqdZ8NUu7
If you haven't yet, make sure that you add Azure as a Connected App in Defender for Cloud Apps: Connect Azure - Microsoft Defender for Cloud Apps
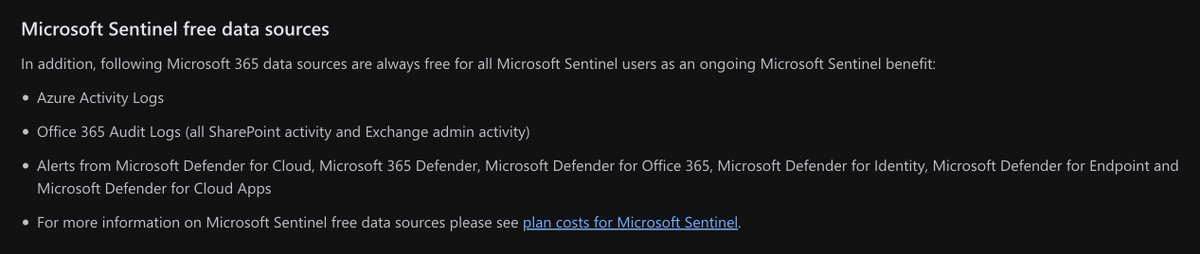
And finally, if you haven't yet, create a Log Analytics Workspace, add Sentinel, and ingest Azure activity logs (and O365 Management events) for FREE :)

A few folks mentioned management groups and landing zones. They're more architecture related, requires planning, but still important 🙂
Management groups let us organize subscriptions (kind of like OUs) and apply RBAC and Azure policy through inheritance. Landing zones provide scaffolding to build out resources following some best practices, such as a Log Analytics Workspace with log ingestion configured by policy, RBAC, Azure policy, CI/CD, and network design (like hub/spoke architecture).
I find it too complex when starting out, so play with single subscription first.
